--Originally published at Mental Droppings of a Tired Student
Since last week Denial of Service attacks was suddenly “a thing” in most media outlets, I thought it was good timing to drop this mastery post related to the topic.
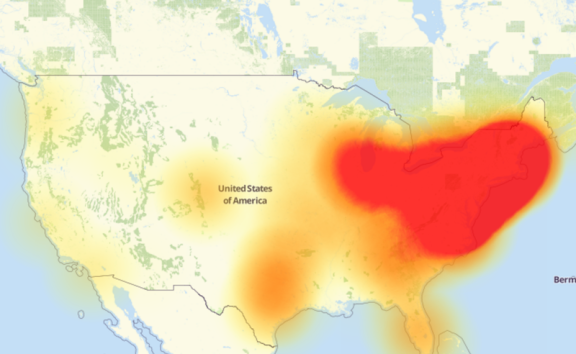
Unless you are living under a rock you heard about the attacks beginning in the morning of last Friday (October 21, 2016) and stretching into the afternoon. The attack involved multiple DOS attacks targeting systems operated by DNS provider Dyn. This massive DOS attack shut down major websites across the internet, Dyn was hit by at least three apparently targeted strikes. The affected websites included Twitter, Reddit, GitHub, Amazon, Netflix, Spotify, Runescape… (who even plays that anymore?), amongst others. Dyn confirmed it was under attack the morning of said events.

This was their statement:
“Starting at 11:10 UTC on October 21th-Friday 2016 we began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Some customers may experience increased DNS query latency and delayed zone propagation during this time. Updates will be posted as information becomes available.”
We discussed this attack briefly during our Networking class, the professor pointed out how DNS is an obvious target for attack. He also made the point that this kind of thing happens when security is put in the back burner; explaining that engineers generally care about functionality and tend to worry about security later or view security as an added plus. However security, as we’ve learned the hard way, should be just as crucial as functionality.
Dyn claimed the problems were mainly affecting customers on the United States East Coast. I was going to say, I didn’t even feel the attack or witness it firsthand at all. I mainly used cisco’s spark, youtube and facebook, who were not under attack.