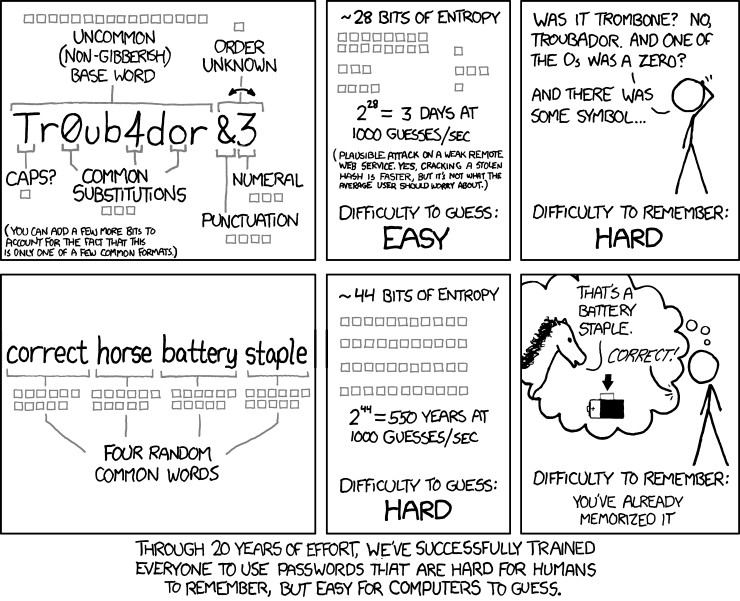
--Originally published at TC2027 – Blog will Tear us Apart
First of all, sorry for taking so long on this post. Writing something personal has always been quite difficult for me, but actually that’s what this is about.
This past semester I enrolled in a course about digital security and privacy, a pretty different and unique course. I knew already who was teaching it, so I enrolled well informed of the teacher’s perspective to teaching: Flipped Classrooms.
My experiences with open and flipped classrooms are always fruitful, maybe my habits, personality and mentality fits this style. Being able to discover by my own (with proper guidance) and learn from things in a way that costed me not only reading and search skills, but also the skill to craft and find the right questions, it’s incomparable.
I know school is finite. My days soon will be over, and the skill I value the most is the one I learned from this kind of courses, being autodidact. Sure, the teacher is there, and hell, he was always, always, ALWAYS, watching. But the freedom was there too, we were told to select from a list of topics and investigate, discuss, ask on twitter, go into the darkest subreddits, and things of such. This allowed me to enjoy and focus on the process and experience of learning, rather than the topic itself.
Sure, I learned about the topic, and I learned a lot. But that depended on me and my own effort. I saw many classmates having trouble deciding what to do without a list of little weekly tasks, and they complained, quite a lot. But let me tell you guys something, the world will never give you a list of activities to do. In a job, they will give you a problem to solve, and your boss will expect you to solve