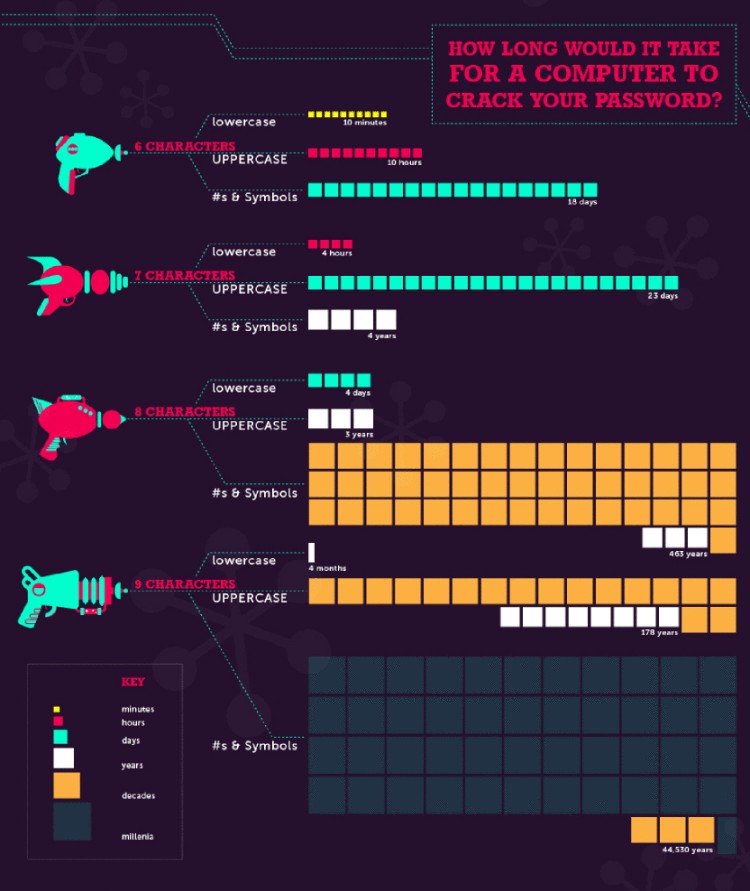
--Originally published at Miss F.
Throughout my soon-ending school experience, I always thought that getting good grades was the only way to learn. I hadn’t had trouble with that until 2012, the year I became a University student. My grades dropped, I started failing subjects, my scholarship was reduced and, consequently, I had a personal crisis. It seemed obvious to me that I was becoming a failure and my life would suck forever because I just couldn’t get my average to what I wanted. My brain was going into shock and I couldn’t soak in any knowledge. I can summarize said experience with this song:
Many students believe that their grades define who they are and who they will become. If you have good grades you’ll be successful and get a good job, if they aren’t you suck. Thus, “I Must Impress My Professor” becomes a hymn.
It wasn’t until less than a year ago that I started seeing things differently. I started loving my degree and my subjects, I began feeling happy about myself and what I had accomplished. Who cares about grades when I have so much more to offer? I clearly remember a few months ago when I called my mum and told her “I think I’m finally getting the hang of school”. She laughed and said “Well, better late than never!”. It literally took me 19 years to understand what school was all about, or at least what it should be about.
A huge part of this change of mind I had, I owe to Ken Bauer and every other teacher that focused on helping students learn instead of showing off and acting as a deity. It’s because of you that I understood that everyone has their own learning process and it’s OK to take longer to understand something and it’s OK not


















 I spent my morning waiting for the internet people to arrive and later on I geeked out on my Wireless Network course❤. I literally had Amy’s look the whole time during said course. And my boyfriend, of course, had Sheldon’s look…
I spent my morning waiting for the internet people to arrive and later on I geeked out on my Wireless Network course❤. I literally had Amy’s look the whole time during said course. And my boyfriend, of course, had Sheldon’s look…