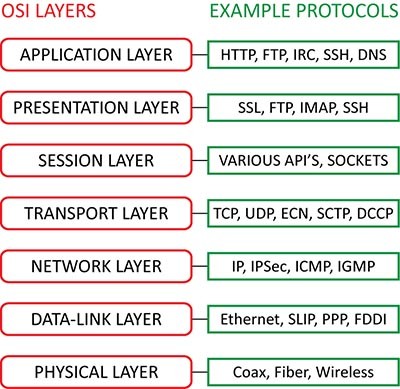
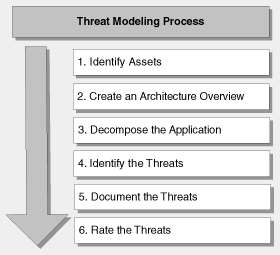
--Originally published at TC2027 – Will It Blog?
I think the method intended to use in the course was good but it has also room for improvement. Through the semester, I did the effort to keep it up with it and learned stuff but I’m not quite convinced yet if it was the best choice to learn this kind of subject.
Here are the things that I perceived from this class that could help improve it.
- Discussions on class: I think they fell short because there was a lack of organization, we can have discussions where everyone could participate if we first preestablish the topics to be discussed on class and ask for a blog post related to certain topic before, having everyone write from different sources but also coming to the class to centralize the knowledge, learn what others wrote about and from that coming to a conclusion would have been more effective to me.
- Writing blog posts: It was ok to me, but I have to admit that after writing that many (20 in total throughout the course) it becomes a bit monotonous, similar to writing an essay.
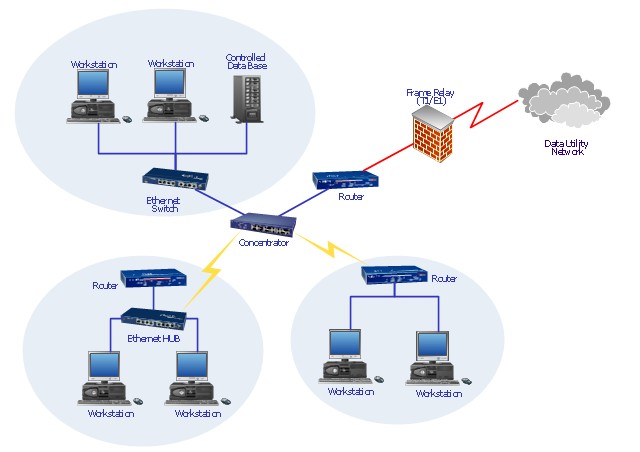
- Lab practices: I think some of them were not that well landed in accordance with the course topics. Also I would have appreciated a bit more problem-solving-challenging style kind of practices, because I think some of them just limited to just install things but not see their actual application on real scenarios. Preparing some dynamic activity/lab practice that required us to use those tools would have been a much better approach.
Leaving aside my personal opinions from this method and class I have to admit that great blog posts (related and unrelated to the course) from great classmates came out as a result from it. The thinks I liked where: using twitter and the freedom in general to