--Originally published at Miss F.
Passwords, the ones that keep our stuff safe. Or do they? In this particular blog post, I’ll be discussing the most known/common methods for cracking passwords.

It’s not uncommon for us to hear someone complaining about how an account of theirs was “hacked”. What they usually mean by that is that someone gained access to their profile and changed stuff while being there. In order to gain access into any system, you need to first crack the password. The following are 10 methods for obtaining someone’s password:
- Brute-force
- This is the most common method of them all. It consists of trying several alpha-numeric combinations until you get the right one.
- It’s simple to program, but it can be very slow if your GPU isn’t your ally.
- Examples of programs that use this methodology are:
- Wfuzz
- Medusa
- Rarcrack

- Dictionary
- As its name says so, this method uses a file which contains words typically stored in a dictionary (and some others like the most used passwords) to search for the real password you’re trying to crack.
- While it’s faster than the brute-force method, this one’s calculating time may vary from immediately to billions of years. This depends on the password’s length, combination and character usage.
- Examples of programs that use it are:
- Cain and Abel
- John the Ripper
- L0phtCrack
- Rainbow Tables
- Rainbow tables are a very elegant way for cracking a password. They consist of a series of lists of pre-compiled hashes (click the link to read more about hashing). These lists are the hashes of all possible password combinations for any hashing algorithm.
- It takes way less time than the two previous methods, however it requires a LOT of GPU power. If a password is salted (with random extra characters), it may be impossible for a Rainbow Table to crack it.



 that use them are:
that use them are:
- OphCrack
- RainbowCrack

- Phishing
- We’ve all heard of this. Phishing is when a hacker creates a mirrored site and steals information from it. This means that the hacker creates a site that looks and behaves exactly like a bank’s webpage, a social media log in or your e-mail account log in. The user rarely realizes it’s fake until it’s too late and have already given their data to the hacker.
- Social Engineering
- A hacker in disguise. They make the user believe they’re talking to the IT department or to an authority figure in order to get their data. If you can get a password without having to do anything at all, why bother?
- Malware
- Another popular term. Malware is, by definition, malicious software; it finds its way into your computer and browser files and steals as much information as it finds.
- Malware can also install key loggers and screen scrapers to see what the user is typing all the time.

- Offline cracking
- Surprisingly, this is the most common way of obtaining someone’s password. It’s rather simple: when a system is compromised (eg: when your phone’s unlocking attempts have exceeded the limit and it blocks itself), hackers are able to physically access the system servers, user password’s hash files, etc (normally through a third party). Once there, they can take as much time as they want until the password is cracked.
- Shoulder surfing
- Pro hackers in disguise. They enter a company by looking just like another employee and taking notes of everything they see. Many, many people stick post-it’s to their computers’ screen with their username and password in order to never forget them. If you ever do this you must know that hackers never forget either.

- Spidering
- Corporate passwords usually are made up by words connected to the business. If a hacker informs him/herself of the common in-company lingo, he/she will include these words into their dictionary file, their Rainbow Table or try to brute-force the system into letting them in.
- Guess
- When in doubt, just take a guess. If you get to know your target a bit better, you’ll discover potential passwords with every word they say. Social media is the place to be when trying to guess a password, everyone unconsciously talks about them.
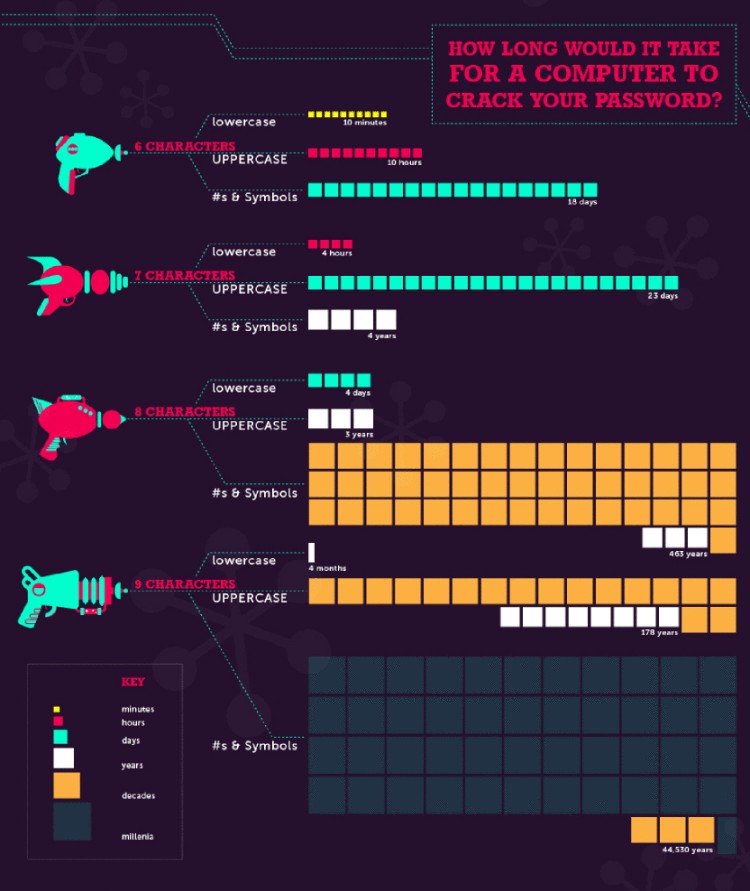
It’s scary how easy it is to crack some passwords. The following is an info graphic that shows how long it takes to crack passwords depending on their length and their usage of lowercase/uppercase letters as well as numbers and symbols.

Image obtained here: http://www.cryptocoinsnews.com/motor-memory-passphrase/
As you see, cracking passwords isn’t really complicated if the password isn’t correctly created. For information on how to create a proper password and more safety tips go to Rubiology’s post! He’s got tons of methods for preventing attacks and, if you weren’t convinced already, he’s also got Tom Cruise.
For more information on how each method works and what programs exist check these pages out (it’s were I got most of my info from):
- http://www.alphr.com/features/371158/top-ten-password-cracking-techniques
- http://www.infosecisland.com/blogview/18538-Top-Ten-Password-Cracking-Methods.html


