--Originally published at (Not so) Random talk

Today, coming down our runway are the security architectures, showing us their models. Show your enthusiasm and let’s begin!
*cue sassy music in*
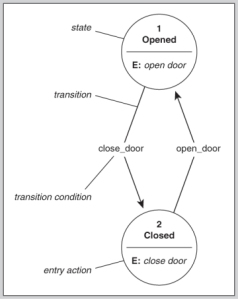
The first model is State Machine. It is using states to verify the security of a system, capturing all the current permissions and instances of subjects accessing objects. Getting the job done, it is dealing with each subject’s association with objects. If the subjects can only access objects by means that are concurrent with the security policy, the system is secure. To alter a state, a transition (activity) must happen, though if all activities do not comprise the system and put It into an insecure state, then the system executes a secure state machine model. If a secure state fails, safety measures like a reboot or system freeze must happen in order to protect the system, itself, and data. As you can see, this is a very basic attire.
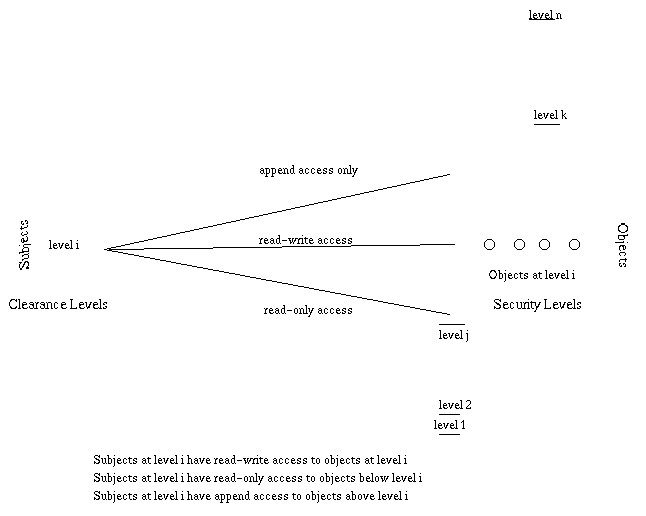
And just as we were saying this, the next Bell-LaPadula model indeed takes the prior basic attire and modifies it into its own style. It is a multilevel security style, with users of different clearences using the system and the system process data with different classifications, and it is an implementation of its predecessor that enforces confidentiality aspects in access control. Its’ goal? Enforce secrets and prevent data leakage. A matrix and security levels are used to determine if subjects can access different objects. The subject’s clearance is compared to the object’s classification; if the clearance is higher or equal to the object’s classification, the subject can access the object without violating the security policy. If properly implemented and enforced, this model has been mathematically proven to prevent data from a higher security level from flowing to a lower security level. It is an information flow




And once more, just after seeing the model, we are brought upon another one who used the model and took it to the next level. Going down the runway now is the Biba Model. This style is more concerned on the integrity of the information within a system, preventing it from flowing to flow into a higher integrity level. To do so, it states two rules: the no write up – states that a subject cannot write data to an object at a higher integrity level – and the no read down – states that a subject cannot read data from a lower integrity level. Pretty simple styling huh? Also, this model seems somewhat more commercial than the past one.

Coming right up is the Clark-Wilson Model, and it seems to take a different approach than it’s predecessors. It focuses on preventing authorized users from making unauthorized modification of data, or commit fraud and errors within commercial applications. If a user wanted to access an object, it would have to access through an application – nice, an accessory! And one that provides another layer of protection and further restrictions in actions! Each program has its own set of restrictions dictating what actions the users can and cannot perform on objects. This style (model) also prevents authorized users from making improper modifications by enforcing separation of duties, and maintains an audit log for external transactions.

Now under the spotlights is the Information Flow Model, which is actually more like a complement to the Bell-LaPadula and Biba models, or more like something from which this two models are built on. In this style, Information is restricted in its flow to only go to and from entities in a way that does not negate the security policy.
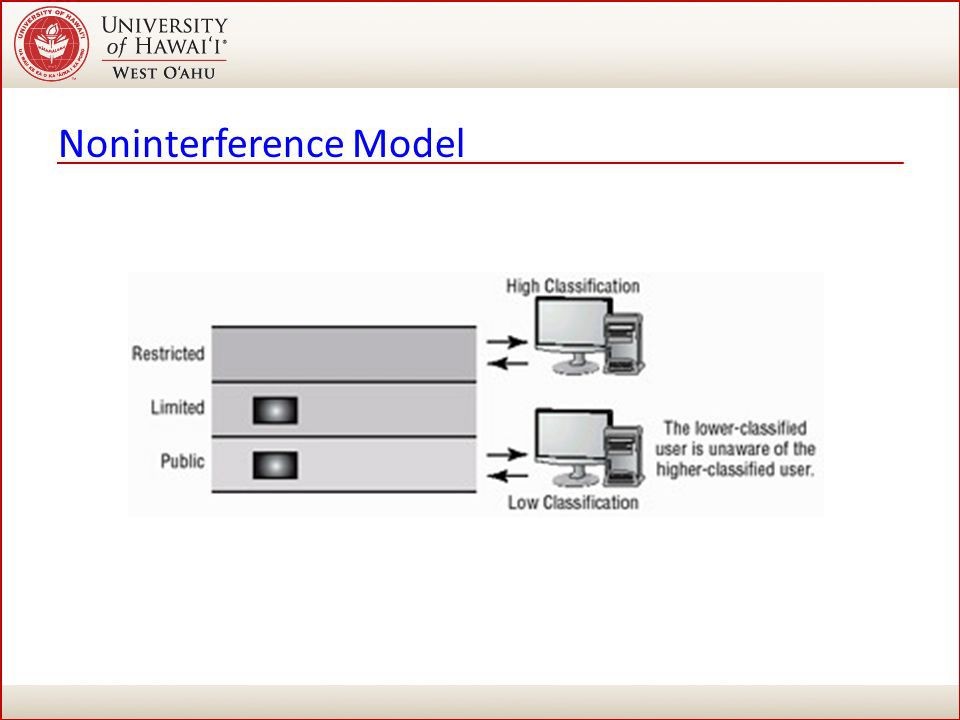
Walking now down the runway is the Noninterference Model. This concept is implemented to ensure that any actions that take place at a higher security level do not affect, or interfere, with actions that take place at a lower level. This type of model does not concern itself with the flow of data, but with what a subject knows about the state of the system. So if an entity at a higher security level performs an action, it cannot change the state for the entity at the lower level. Users at a lower security level should not be aware of the commands executed by users at a higher level and should not be affected by those commands in any way.

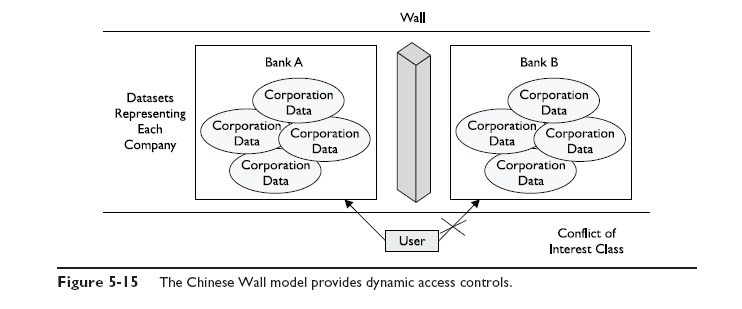
And last but not least, here is the Brewer and Nash Model, called also the Chinese Wall model. It was designed to provide access controls that can change dynamically depending upon a user’s previous actions. The main goal of the model is to protect against users accessing data that could be seen as conflicts of interest.

And that’s all everybody. Great models for the season of security don’t you think? Let´s give the models a round of applause as they make a final appearance down the runway, being this the last words from yours truly. Until the next one everybody!
Post made in collaboration with Miguel. Go check out his posts, they are cool!
Reference:
http://media.techtarget.com/searchSecurity/downloads/29667C05.pdf


