--Originally published at TC2027 – Will It Blog?
A network is done when two or more machines are connected together and sharing resources. The internet is not more than a network of networks. Right now I’m going to focus in wired networks security. The wire used to connect two computers using the Ethernet protocol is called UTP (Unshielded Twisted Pair). This commonly are connected to switches which are connected to Routers, this is the basic scheme of a network.
Also neat network wiring looks really awesome, just like the armor of an Eva Unit.

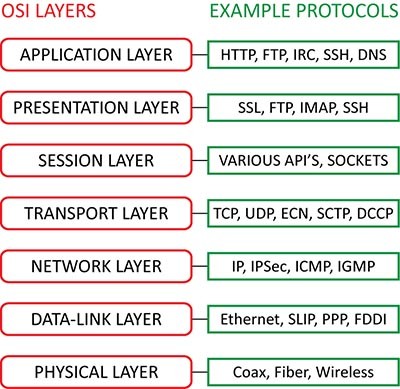
Back to the topic, common vulnerability is unauthorized access, which well the term explain itself. If the attacker gains access it can exploits several vulnerabilities. Tthe following are a list of vulnerabilities found in several of the parts that conform a network. I will require that you already know what the Layers of the OSI Model are and what sort of protocols are used at each level (I will leave a diagram just in case).
Vulnerabilities inside TCP/IP Protocol
This is the protocol suite (group of protocols) in which the internet is builded on. One of the protocols that runs in this model is the TCP protocol which has a vulnerability in the three way handshake done when establishing a new connection, an attacker can open a half open session through tons of SYN messages, this would eventually flood the server and make it crash, also IP spoofing attacks can be done through the network (like the ping of death) used in DoS attacks.
Vulnerabilities in the DNS
The Domain Name Server the one in charge of resolving host names into ip addresses also has vulnerabilities that could be exploited. This program can be attacked to modify its records and redirect traffic to an incorrect or malicious IP address, this goes by the name

Vulnerabilities on the ICMP
Stands for Internet Control Management Protocol, it is used on a network to send error and control messages of devices. ICMP can be used by an attacker to discover the network topology and the hosts on it. There are some utilities that use ICMP such as the command traceroute in Windows, again it can be used to discover topology structure
Vulnerability on the ARP
Address Resolution Protocol. Maps IP addresses intro a physical machine address (MAC). ARP can be spoofed by an attacker, this way the attacker can intercept the data frames on a network, modify them or stop them. With this power the attacker can now launch attacks like
Firewalls are useful measure to help improve security.
https://www.tutorialspoint.com/network_security/network_security_overview.htm
http://www.interhack.net/pubs/network-security/


