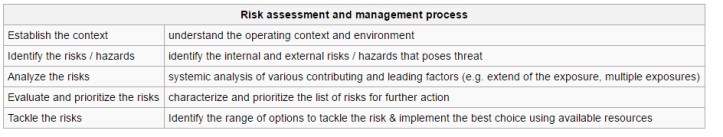
--Originally published at Mental Droppings of a Tired Student
In all types of engineering, sophisticated risk assessments are often used within companies when it concerns threats to life, environment or machine functioning. The nuclear, aerospace, oil, rail and military industries have a long history of dealing with risk assessment. Medical, hospital, social service and food industries control risks and perform risk assessments on a continual basis. Methods for assessment of risk may differ between industries and whether it pertains to general financial decisions or environmental, ecological, or public health risk assessment.
Risk assessment is the determination of quantitative or qualitative estimate of risk related to a well-defined situation and a recognized threat. Quantitative risk assessment requires calculations of two components of risk:
- The magnitude of the potential loss (L)
- The probability (p) that the loss will occur.
An acceptable risk is a risk that is understood and tolerated usually because the cost or difficulty of implementing an effective countermeasure for the associated vulnerability exceeds the expectation of loss.
Part of the difficulty in risk management is that both the quantities by which risk assessment is concerned (potential loss and probability of occurrence) can be very difficult to measure. The chance of error in measuring these two concepts is high.

The following methodologies that are commonly used by security
practitioners and consultants for risk assessment:
- Asset Audit
- Pipeline Model
- Attack Tree
Asset Audit
The asset audit approach is an easy-to-use and straightforward method for
assessing risks by giving the reviewer and owners a direct approach of looking at
all the information assets and their risk exposure. The people involved in the
asset audit process also obtain a better understanding of how information flows
in and out of, as well as, is stored on the system. With this knowledge and insight
of the system and the information flow, the reviewer can have

what and where are at risk and thus needs to be protected.
Pipeline Model
In this approach, risks are assessed on a pipeline, which is the system constituent that is responsible for processing a certain type of transaction. Each pipeline is made up of five components, as follows:
- active processes – all the software that make the transaction happen
- communication processes – responsible for sending/receiving messages (data) over the networks
- stable data processes – responsible for inserting stable information into
the pipeline - enquiry processes – responsible for extracting information from the pipeline
- access control processes – responsible for controlling human access to the pipeline
The security requirements for each pipeline are derived from the security policy
of the organisation. Each pipeline is reviewed according to the five components
to determine whether the security requirements are met and if not what are the
gaps that need to be addressed.
Attack Trees
Attack trees are a variation of fault trees. Attack trees provide a methodical way of
describing the security of systems based on who, when, how, why and with what
probability an attack will happen. The top of the attack tree or its root node
represents the ultimate goal of the attacker and the branches and leaf nodes show
the different ways of attaining the goal.
The attack tree method of risk assessment may not be suitable for a novice
security reviewer who may not have enough experience and knowledge to have
the insight needed to identify all the different attack methods that would be used
by different attackers.
References
[1]-https://www.giac.org/paper/gsec/3287/overview-practical-risk-assessment-methodologies/105426
[2]-https://en.wikipedia.org/wiki/Risk_assessment