--Originally published at TC2027 – Will It Blog?
First of all I would like to say this was a post in collaboration with two other people: Cesar Cornejo and Audray (Ariadna)
About everybody knows by now that systems need security in order to protect data from access of unauthorized users or malicious programs. Operating Systems are no exception to this rule.

Another characteristic of Operating Systems aside from performing hardware abstractions and sharing/coordinating data among processes, is that they also need to ensure security on each one of its resources such as CPU, disk memory, ram memory, programs and information or data that programs use.
UNIX/Linux
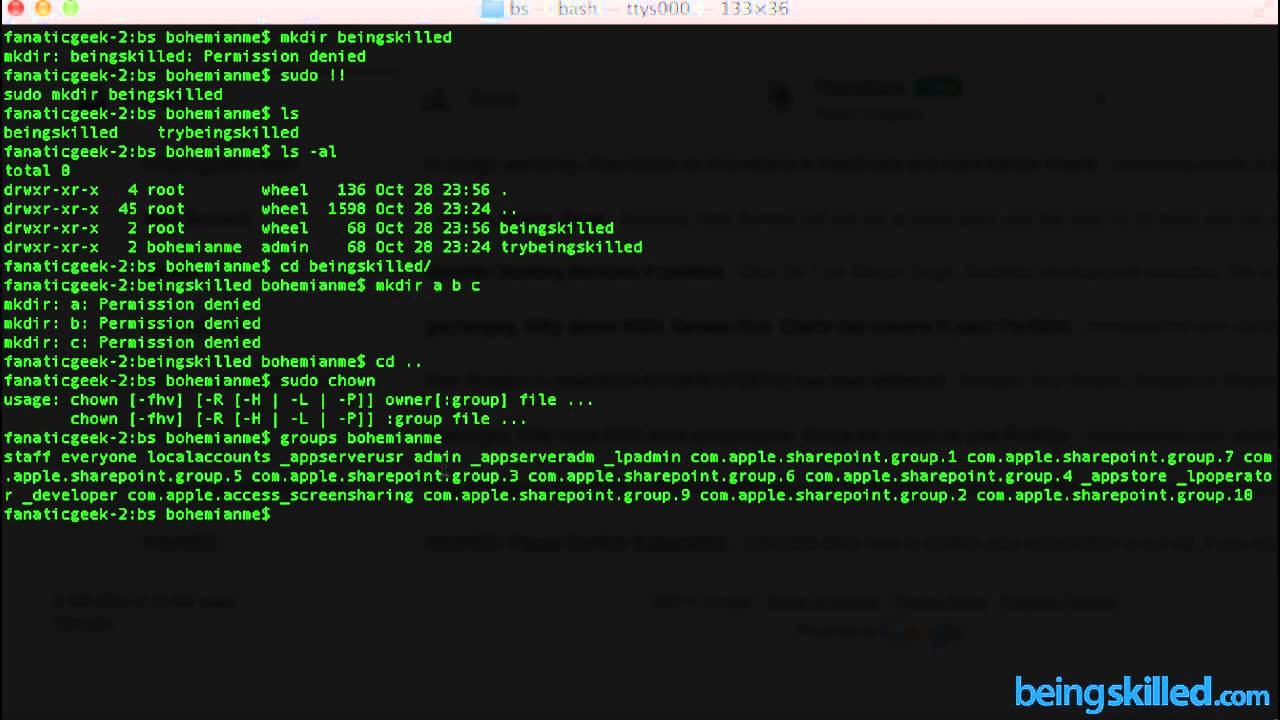
How do they achieve this? For example In UNIX systems at the most low level inside we have three protection domains available: owner, group and global. For each domain three operations are allowed over a certain resource and those are either reading (r), writing and executing (x). So only the superuser (or the sudo user) can change resource settings in order to manage the permissions over those resources, the type of session that is allowed to use them and what are they allowed to do with them.
Mac OS
On other hand, Apple’s Mac OS X implements extra layer security like:
- Application Firewall which lets you control the connections made to your computer by others.
- Gatekeeper which can block, in previous configuration, any install aside from the apps made by Apple.
- XProtect which compares any downloaded file with a blacklist made by Apple of known malware.
This extra security measures can make a big difference to the average user of any computer and having them running by default is a big plus to not worry with technical issues.

We can make an extra comment about an usual myth: Neither Mac’s nor Unix’s can’t get virus.It’s a lie, both of them can


Windows OS
And last but not least, we have Windows. I think most have heard either good and bad things about the security in Windows (though it may also be because it is the most used OS). The most known way Windows achieves security is by having two types of users:
Local users & Administrator
Though most of the times the main account, or administrator account, is the one we normally use, but it will still ask you if you want to really do something like installing a program. But there is another way to give or revoke privileges to standard users, and that is by “user rights”. When a user is added to one of the groups they get extra power to do more than the standard user, they get extra User Rights. These are the rights or configurations that control “who” can do “what” to the computer. When configured, each computer can support a unique set of administrators controlling different areas of that computer.

There are over 35 user rights per computer, which are deployed using Group Policy. Some of the most common user rights that control elevated privileges over a computer are:
– Shut down the system
– Force shutdown of remote system
– Log on as a batch job
– Log on as a service
– Backup and Restore files and directories.
Also, each file, folder or key have Access Control Lists (ACL), which can give permissions for read only, modify or full control.
So now you know in which way your OS protects its data by creating different user types of groups and the kind of privileges each has. As many things in security, it ultimately depends on you, common user, on how you will use this power. Remember: “With great power comes great responsibility”.
http://www.nebrija.es/~jmaestro/AT3148/Seguridad.pdf
http://www.howtogeek.com/217043/xprotect-explained-how-your-macs-built-in-anti-malware-works/


