--Originally published at The shield of the world
As you can imagine we are talking something related to computer security. This time is countermeasures, which is an action, device, procedure, technique or anything that can reduce a thread, a vulnerability, or an attack by eliminating or preventing it, by minimizing the harm it can cause, or by discovering and reporting so a corrective action can be taken.
So a threat is a possible violation of security, which exist when there is a circumstance, capability, action or event that could breach security and causa harm. A threat is a possible danger that might exploit a vulnerability. A threat can be either intentional or accidental, so you have to be prepared for both of them.

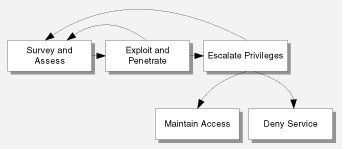
So if we know the anatomy of an attack is easier for us to defend ourselves from an attack. So let’s see the anatomy:
- Survey and assess
- Exploit and penetrate
- Escalate privileges
- Maintain access
- Deny service
We were talking with our professor and then he says something special for this topic “In the moment you tell me which OS and version are you using, you are really exposed” or something like that, the main point is that when someone knows which software are you using, is way easier for them to attack you. So, explicit countermeasure number 1…don’t share your software information.
Survey and assess
But, why is so important for the attackers to know which software are we using? Because, they can know the supported services, protocols, ports, vulnerabilities and entry points…a whole bunch of information.
Exploit and penetrate
And just to share something with you, if you actually have a good protection in the network and host, the next gate is your application. For an attacker, the easiest way into application is though the same entrance that legitimate users use.
Escalate privileges
In