--Originally published at TC2027 – Will It Blog?
Yesterday on a workshop about a rapid prototyping tool for making web applications, a classmate asked about the options that the tool offered in order to authenticate users. For that the instructor went along to ask us if we knew the difference between authentication and authorization.
An easy way to differentiate both is to make two questions. Who’s allowed to log in? (authentication) and once the user is already logged into the system, what is he allowed to do? (authorization). That just comes as an introduction in order to talk about the different types of authentication that exist out there, it is not important to remember all of them exactly but if you can read them once you will know what can be done in order to accomplish a reliable authentication method.
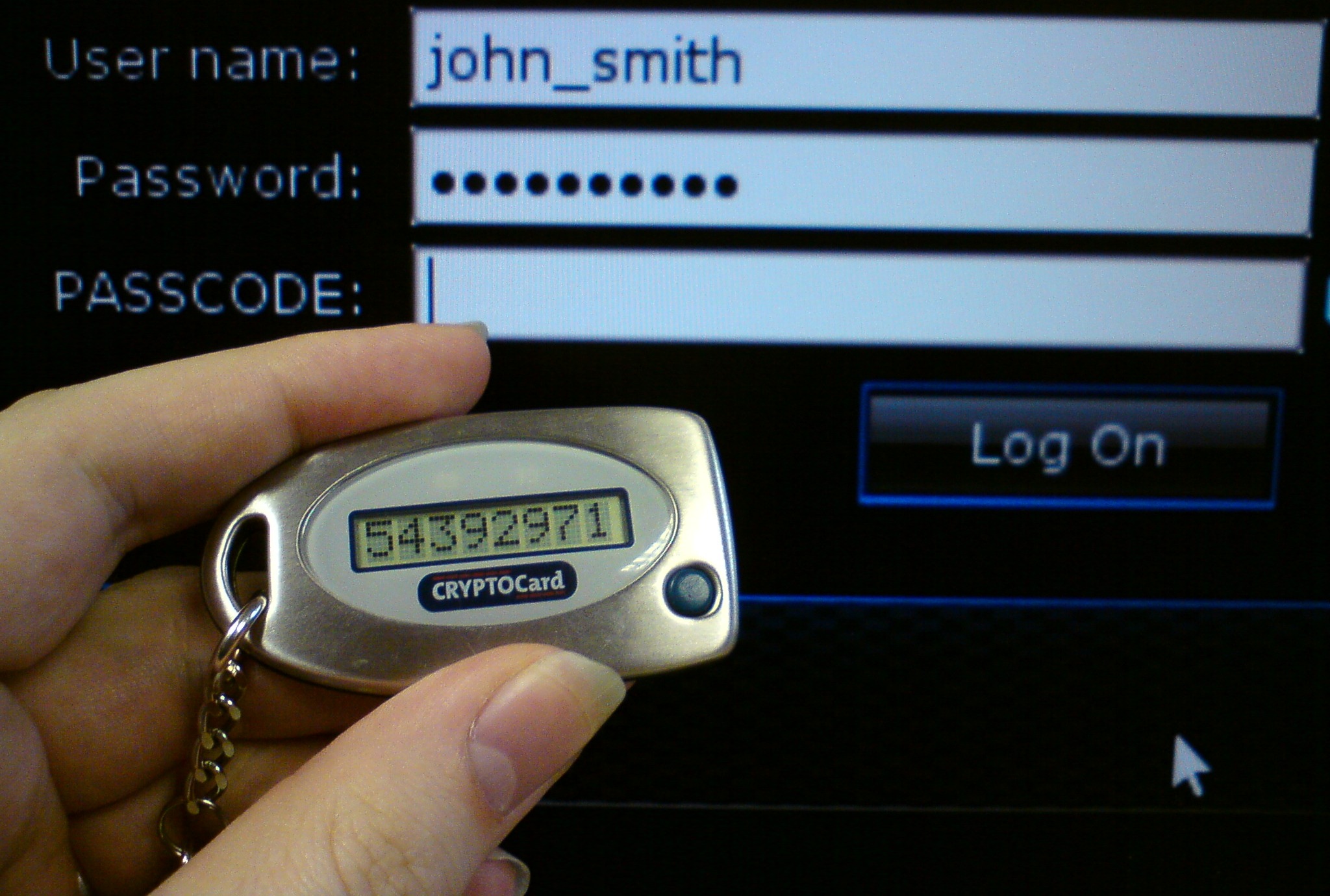
In most kind of systems you identify yourself with some kind of identifier (usernames, emails) followed by a password, that is the most common authentication method and it is called PAP (Pen Apple Pen, just kidding it stands for Password Authentication Protocol). At the most basic level you will have the server looking for these values on the tables and if there exists a record then grant access.
Challenge Handshake Authentication Protocol (CHAP)
In this method the server in charge of the authentication process sends the user an ID and a random number, also the sender and receiving program share a predefined secret word.
So the client strings together ID + generated random + secret word, in order to make a key that can be hashed, this retrieves a new value. This new value is sent to the authenticator, which now has the job to compare it with a built string made by itself using the same hash.
Mutual Authentication
Also known as two way-authentication.