--Originally published at Diego's Password
A security model provides all the specifics for a given architecture. It describes specifically how will the system logic will be implemented and executed. It will display all the bones needed to support the complete body; it will provide the fences and bars structures in a prison, it will… Ok enough! It’s very clear ok! There’s another important aspect called security policy, and they work together. The security policy describes what or which aspects will the architecture protect or secure, like the requisites; while the security architecture provides the how and where, the technical arrangement of the components.
Without further ado, lets discuss the classic security models.
- State Machine Model
Remember our class Computational Mathematics? Remember how automatons worked? It’s a machine which is structured with it’s own states and transactions. Well, a state machine model describes in a architecture in a similar fashion, if all the states and transitions remain secure, if and only if all of them at all time, then its a secure state machine. Very simple to describe, hard to accomplish.
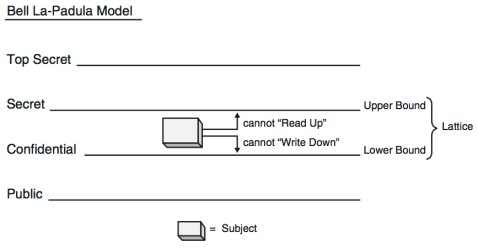
- Bell-LaPadula Model
This model was created int the early 70s by the US military. They were the first ones to implement secure state machine models. They found out that there was a lot of data leak out of their control; since they had very sensitive data, they were concerned about the privacy and reach of it. So they created the idea of having classification of users and data within the same system. The information was divides into categories like top secret, being the most delicate data, to secret, confidential and all the way up to public. All the users had something called “lattice” which was a couple of bounds describing their access level over the data, upper and lower. It’s pretty obvious but the user
 be able to read or write anything outside them, specifically the upper bound limited the read access and the lower bound the write access. It’s pretty simple to understand and it might even sound a bit to obvious but at the time it was a revolutionary idea, just to conceive this attribute or classification to a peace of information was completely out of their minds.
be able to read or write anything outside them, specifically the upper bound limited the read access and the lower bound the write access. It’s pretty simple to understand and it might even sound a bit to obvious but at the time it was a revolutionary idea, just to conceive this attribute or classification to a peace of information was completely out of their minds.
Its important to mention that this model only controls data access but not integrity, we’ll see in the next one how it takes control over that area.
- Biba Model
While the previous model provides confidentiality Biba provides integrity. This is very similar to the previous one. It follows the same principal state machine and the confidentiality. What differentiates them are two rules. You can only write at your level, or bellow; meaning that there’s no write access to uppers levels. The second one being, you can not read from lower levels. How can these changes protect the integrity? Simple, if you’re not able to read lower levels, there won’t be any corruption of data. Probably this example will make more clear. Imagine you are making a school research. You shouldn’t look for older or not official sources right? They might be outdated and you don’t know where the data came from, you cannot mix your reseat with a higher level with articles from lower levels.
- Clark-Wilson Model
In this model something really innovative was implemented, access triple. Instead of having the user accusing directly to the data, a third component is added in the equation, and application. Incredible right!? This way you prevent unauthorized access and improper modifications.
- Information Flow Model
It basically takes care of the confidentiality and integrity at the same time. It checks for any data flow operation that happened within different levels, checks a matrix and asks if that specific permission was granted.
- Noninterference Model
It makes a division from the levels when something happens. If the user alters a given level, the lower levels should not be able to see that change, so everything remains secret to users with lower access.
- Brewer and Nash Model
Creates the ability of changing the level of access of the users, hence when the situation change, you can modify the access to specific data to a given user.
I found these models very interesting. While I was reading through them I learned a lot of the history of information security and how it was evolving. Now it seams so obvios to have a third layer or to have levels of access but I find impressive how these people came with the idea, of course it was based on their needs but anyways it is such an advance.
Source
CISSP Certification All-in-One Exam Guide
http://media.techtarget.com/searchSecurity/downloads/29667C05.pdf