--Originally published at TC2027SWSecurity
We could define fake news as falsely descriptive information that seeks to manipulate the audience regardless of its purpose.
Although using fake news to manipulate the public is a thousand year old practice, this new iteration we call fake news is much more powerful because of its speed, power and low production cost. The fake news is a kind of cancer of the web that is born as a result of the business models of Google and Facebook, in conjunction with the decline of traditional media.

To face it, then, what we need are better professional means that inspire confidence and seriousness, that win over the audience with courageous and objective coverage, taking advantage of both technology and historical journalistic techniques. If we can not value journalistic work seriously, making both readers and platforms pay for good content, then we will end up hurting ourselves, living in a less informed society and therefore less free.
Source: fakenews source
Gilberto Rogel García A01630171 #tc2027








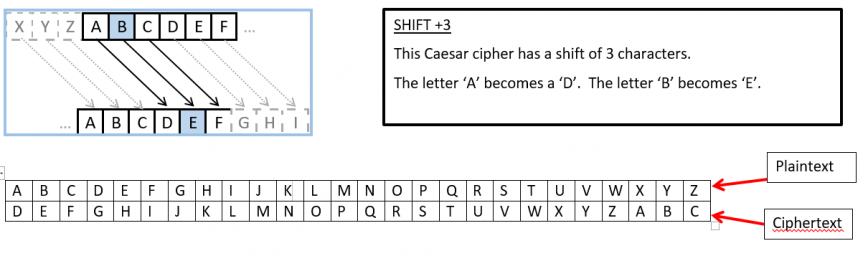

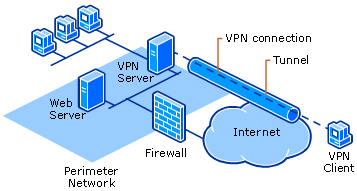


 Here’s a website claiming which are the top 5 VPNs: http://top5-vpn.com/hp-id-2/?gclid=CjwKCAiAtorUBRBnEiwAfcp_Yzhx0VZrS3fABj3i8hYXMzgf_q6SHw9-WNUm_BEtsx1Zh239O0M9EBoC_IoQAvD_BwE
Here’s a website claiming which are the top 5 VPNs: http://top5-vpn.com/hp-id-2/?gclid=CjwKCAiAtorUBRBnEiwAfcp_Yzhx0VZrS3fABj3i8hYXMzgf_q6SHw9-WNUm_BEtsx1Zh239O0M9EBoC_IoQAvD_BwE
