--Originally published at Computer and Information Security
Es muy útil saber cómo modificar los ajustes de un módem. Cambiarle la contraseña a la red de la casa o incluso cambiarle el nombre puede llegar a ser muy sencillo y puede a llegar a incrementar un poco la seguridad de la red. Sin embargo, hay más opciones en los ajustes de un módem y éstas pueden llegar a ser implementadas de una manera muy sencilla. Una de las ventajas de acceder a los ajustes de éste es que puedes crear redes locales dentro de la casa o la oficia. La división de la red puede llegar a ser útil para conectar ciertos dispositivos a una de ellas y los otros a la otra, se puede crear una red para invitados, o incluso redes privadas para intentar mantener más segura cierta información que se comparte cuando alguien se encuentra en la misma red. A continuación, se mostrará un pequeño tutorial para crear una nueva red doméstica.
1 – Entrar a la página web del módem
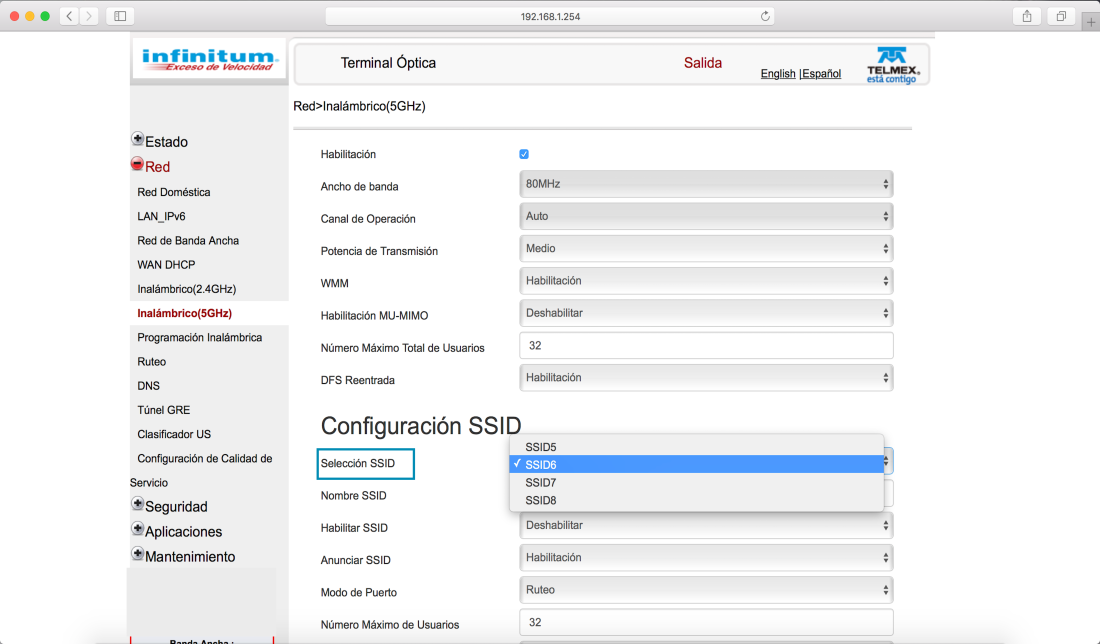
Normalmente, para poder acceder a la configuración del router se tiene que ingresar a la dirección 192.168.X.X. En este caso para ingresar a la configuración del módem de Telmex, se ingresa a 192.168.1.254. El usuario puede variar (TELMEX en este caso) y la contraseña es la clave que viene en el modem.

2 – Ir a Red
Al entrar a la configuración del módem, una ventana parecida aparecerá en la pantalla. Hay que seleccionar la opción de “Red” que se encuentra en la columna izquierda.

3 – Inalámbrico (2.4GHz o 5GHz)
Una vez adentro de la opción de Red, se selecciona el tipo de red inalámbrica que se desea crear el la columna izquierda. En este caso, se seleccionará la red 5GHz.

4 – Seleccionar SSID
En