--Originally published at Computer and Information Security
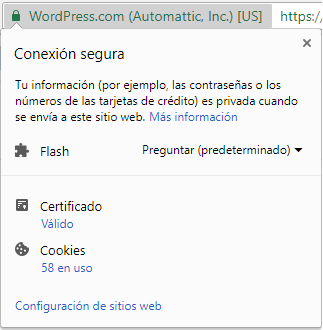
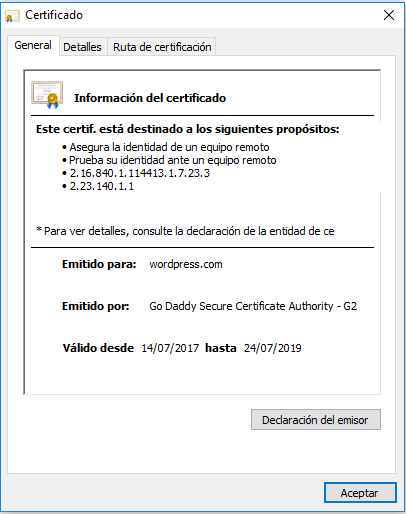
The concept of cryptography can be easy to understand, but not as easy to implement. Cryptography has been around a while now. Today, we hear that word and we imagine a secure program to protect passwords, but it was mainly used for war. First of all, we can define cryptography as an activity to convert an intelligible text into an unintelligible one or all the way around. This method is used to protect information and its main goal is to send and receive this plain text decoded in order to decode it. It is also used for authentication.

The first implementations of cryptography were different compared with the modern ones. Today, cryptography is based on pure complex mathematical approaches. The main goals of it are discussed all over the internet, but the most controversial ones, at least for me, are following ones:
- Confidentiality: confidentiality means that no one can understand the encrypted message but the receiver and only using the tools to decode the message.
- Integrity: it is crucial that no one can be able to alter or modify the integrity of the encrypted message.
- Non-reoudiation: this means the the one that is sending the message cannot deny the content of the message at a later stage. There can’t be differences between what is send and what is received.
- Authentication: authentication can be used to confirm the connection between the one that sends the message and the one who receives it.
There are a lot of advantages regarding cryptography. Banks, computer passwords, and e-commerce transactions use it to protect their information from getting leaked. It is important to say that an encrypted text doesn’t mean that it isn’t crackable, but there a re different ways to measure the effectiveness of an encryption. Normally, they are measured with the amount of Continue reading "Cryptography"