--Originally published at Lord Security
On these days I could get my hands on a really cool device from hak5, the Packet Squirrel, which can be used for an Ethernet man-in-the-middle attack, being able to use it as a sniffer or to get remote access to a network.

This tiny device has a button to turn it in, an Ethernet in port, an Ethernet out port, a microusb por for power, a usb port for storage and a switch to select which of the payloads to run.

The default payloads the packet squirrel has are:
- TCP Dump: . It allows the user to display TCP/IP and other packets being transmitted or received over a network
- DNS Spoof: Alters the DNS directions from the victim to show a different page
- OpenVPN: Provide remote acces to the network or client tuneling
To use de TCP dump you just need to select the first payload, moving the swithc until the left and connect it to the device you want to see the traffic. Then the led will start to flash yellow indicating it is saving the traffic in the usb flash until you push the button to indicate you are done. Finally plug the usb to you PC to see a pcap file, which you can inspect the traffic with a protocol analyzer, like Wireshark.


In the case of the DNS spoof you need to enter the arming mode of the packet squirrel (rightmost side), and configure the spoofhost file with the domain and the ip you want to set.
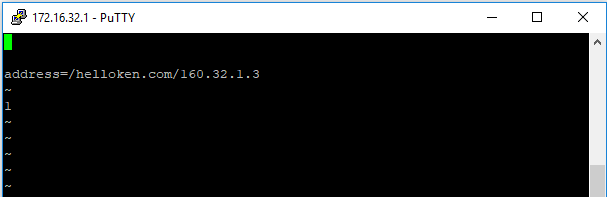
With the OpenVPN you can provide remote access to the network, the target device will have access to the network in the Ethernet out port without interruption, the OpenVPN will be established enabling remote acces to the pcket squirrel
Also it can be used to tunnel the traffic
Continue reading "Packet Squirrel" →









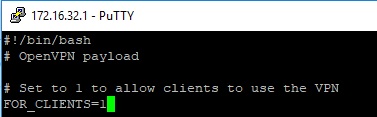






 on mining cryptocoins when you can trick others to make it for you? That’s what the people who use Coinhive think.
on mining cryptocoins when you can trick others to make it for you? That’s what the people who use Coinhive think. That means that when someone visits site with Coinhive on it part of the resources from the device the user is using to browse the page will be used to mine for the person who put the code there.
That means that when someone visits site with Coinhive on it part of the resources from the device the user is using to browse the page will be used to mine for the person who put the code there.