--Originally published at Merino is talking about security.
this isnt't allowed either:
this is allowed:
--Originally published at Merino is talking about security.
--Originally published at Merino is talking about security.
--Originally published at Sebastian Luna
--Originally published at Sebastian Luna



--Originally published at Sebastian Luna
--Originally published at Tc2017-security
Catfishing is when in social media they steal an identity and fake they are someone else. A lot of people have been victims of this people. Some of them have been lucky and found out, before getting hurt, but there are others not so lucky that have fallen in the lies of this people. There are cases where the victim falls in love with ths people and has given them money, or even worse been kidnap. We have to take precaucions and don’t accept or be fooled by any user you don’t know. If you don’t know the user don’t give any of your personal information. In your profil make sure everything is private or that the information you are displaying is alright for you.
Here is an example:
--Originally published at Tc2017-security

Two weeks ago I came back from a hackaton in Dubai due a competition we won last october(the prize was participate into the Dubai’s Mobility Hackaton by Youth For Public Transport). We flew 24 hours from Guadalajara to the event, then we were developing our product(business model, prototype, slides, pitch) and we presented the project to some Dubai’s authorities such as the Dubai Prince, CEO of Careem, CEO of RTA, head of Y4PT among others. Our project was a virtual assistante to move through the city in a clean, fast and sustuinable way, with this we won the 3rd place. It was such an amazing experience to meet people from around the globe and share ideas and see different ways of thinking about the global problems we are living in. After this we presented the project in an expo, in the Dubai World Tarde Centre for a couple of days. It was great to have won a price, but it is more important to me the experience, the possibility to aquire a new global vision and have fun with this amazing experience. We are looking forward to win the next edition of this event next year in Sweden!

--Originally published at Computer and Information Security
Each day, we log into many different webpages, they ask for authentication. We need to prove that we are us, but why is it so important? Also, how does it works? Authentication is needed to access to personal information, social media, at work, unlocking the phone, anywhere. It is almost a requisite to join every webpage to access to certain content. Regarding security, it is the way to block your information for the resto of the world. There are many different ways to prove that you are really you. Commonly, sites ask for a password, but they aren’t the only option. The next video uses interesting examples to explain the importance of authentication.

A modern way to authenticate the user is its location depending on the cellphone. This also has to do within its device activity and many other complex factors. Nowadays, it is recommended to use at least two factor authentications at the time per each account. For example, it is possible to activate an account with password and with a pin provided by the service company via cellphone.
There are may authentication tools in the market. It is important to be secure and also to protect your personal information. It can be annoying to unlock the accounts with more than 1-factor-authentication, but sometimes it is necessary Continue reading "Authentication"
--Originally published at Computer and Information Security
Confidentiality, integrity and availability is also known as the CIA triad. CIA triad is a model that establishes some principles for information security, it can be seen as an organizer. These three principles are considered as the most importan principles for security. They aren’t the only ones, but they can be seen as the three pillars of security. The following video explains very well these three principles:
Confidentiality can be defined as a series of rules that are responsible for preventing information from reaching the wrong hands. That is, confidentiality is in charge of the access. This access must be restricted for those that don’t have the authorization to see the information. One way to prevent a leakage is to create levels. Most of the time, information is categorized depending on the impact it would have if the specific information was stolen.
Integrity is an important pillar to security, it is in charge of the accuracy, consistency and trustworthiness of the information all the time. It is crucial the security of the data. Information can’t be corrupted or edited by a third-party without the autorizaron. Also, while sending data, it must be delivered and received without any modification in between. Software can be involved in order to check the integrity of data that is traveling from one place to another.
Availability is mainly in charge of the hardware. If there are complications between services or any damage, there must be a resource in charge of fixing it. Also, it needs to be updated all the time and there has to be one that establishes de communication between the different services. There must be an adaptive recovery if it is necessary. It is important to have a way out of problems, even without a person in charge for it.

--Originally published at Toledo
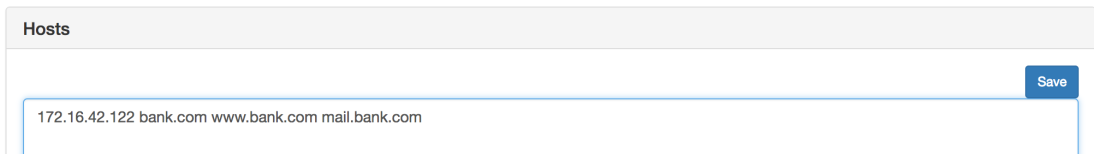
Por sus siglas en inglés DNS, Domain Name System, es un sistema en internet que funciona como directorio. Cuando intentas acceder a alguna página, digamos google.com, lo que sucede por abajo del agua es que la computadora va y pregunta la dirección IP en la que se encuentra el servicio de google.com, ir a consultar dicha dirección. La cual en mi caso es 172.217.9.14.

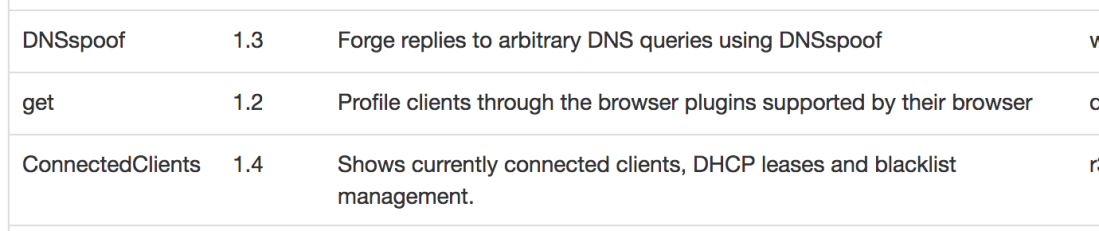
Tambien conocido como DNS Poisoning. Es un tipo de ataque que se aprovecha de las vulnerabilidades de DNS. Con la configuración correcta, quizá un ataque de man-in-the-middle de por medio, es posible personificar servicios conocidos. Puedes direccionar a tu víctima a un servidor de DNS del que tu tengas control, y podrías modificar las direcciones IP de los dominios que consulte.
Antes que nada es necesario terminar la configuración del WiFi Pineapple. En éste blog doy una breve introducción al WiFi Pineapple y explico cómo setearlo.
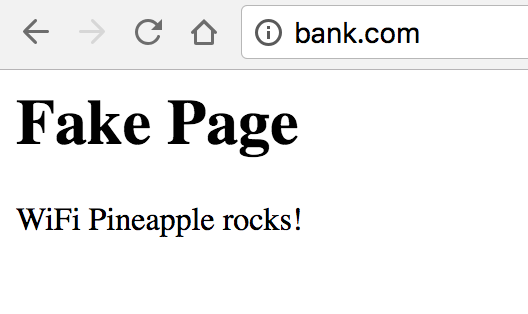
Lo siguiente es tener un sitio de pruebas fake. Como demostración, voy a utilizar el paquete de http.server de python 3 para levantar una paqueña página.
Creamos un archivo llamdo index.html en un directorio nuevo con el contenido:
<head> <\head> <body> <h1>Fake Page</h1> <p>WiFi Pineapple rocks!</p> <\body>
Con la terminal en dicho directorio. Ejecutamos el servidor con python3:
python3 -m http.server 8080
Con ésto deberíamos poder ver nuestra página si utilizamos nuestro navegador para ir a la dirección http://localhost:8080/

Consultamos nuestra IP y le guardamos para utilizarla en los siguientes pasos. Tambien podemos acceder a nuestra página a tráves de ella.

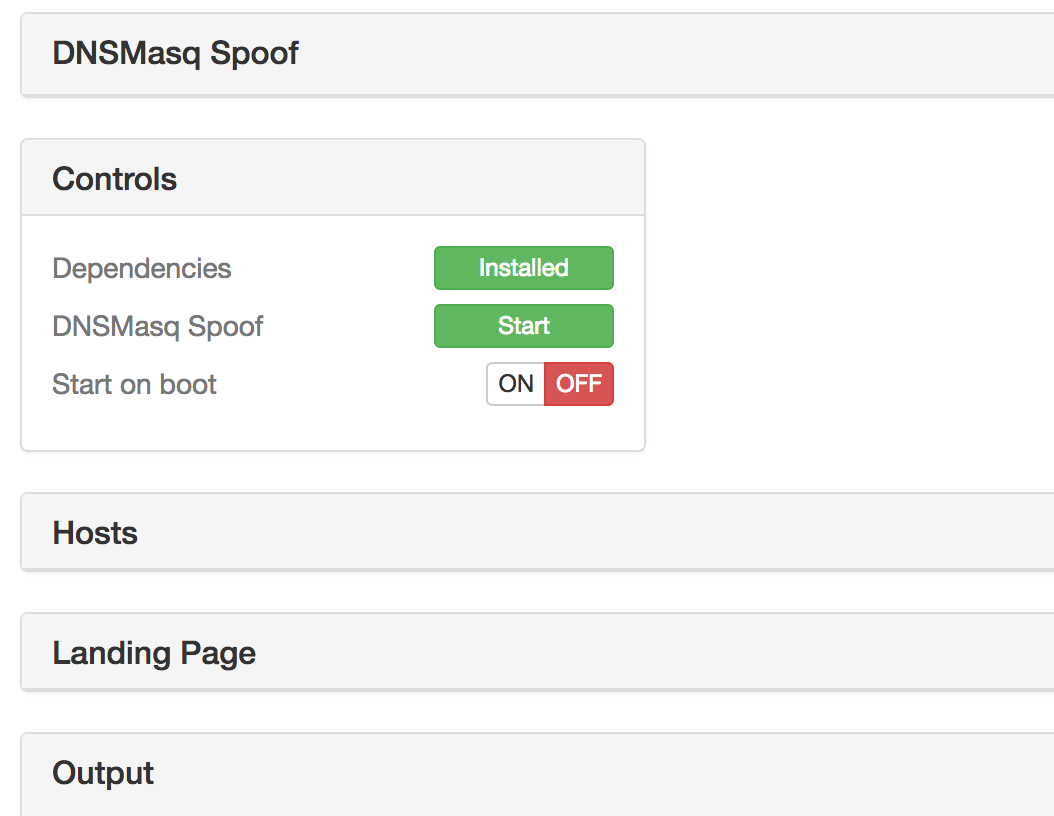
Ingresamos a la interface web del WiFi Pineapple. Por suerte para nosotros, ya hay software desarrollado para el Pineapple para todo tipo de ataques. El DNS Spoofing