--Originally published at Sebastian Luna
Let's wikipedia:
Cryptography is the practice and study of techniques for secure communication from third parties.
It is about constructing and analyzing protocols that prevent unauthorized access to the message.
Modern cryptography is based on mathematics and computer science, thanks to computers, we have the power to encrypt data and make it 'impossible' for a human to decrypt it.
Getting startedThe way I got into cryptography, was with the series "Gravity Falls", they put some hidden messages all over the place, on the intro, at the end of the episode, and they used different encryption methods. It was really fun to try to decypher a code that you found on an episode.
If you know nothing about cryptography, I would recommend to enter the link provided at the end of this document, and to watch the animated series.
Encryption methodsSome encryption methods that were used on Gravity Falls are:
Caesar cipher: substitute the original letter for the nth letter before it. In the case for letters X, Y, and Z, (if n = 3) one would have to cycle through to the beginning of the alphabet.
Atbash cipher: decoded by reversing the letters. (A turns into a Z)
EXAMPLE: World -> D
A1Z26: simple substitution cipher decoded by substituting the nth letter of the alphabet for given number n.
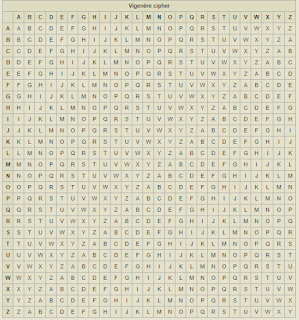
Vigenère cipher: it's a series of Caesar ciphers where each letter shift depends on a key word. Vigenère ciphers use a Vigenère square to encrpyt the message.
These are relatively simple Encryption methods, computers use other methods but I will write about it on another blog, I want this one to be for "begginers".
http://gravityfalls.wikia.com/wiki/List_of_cryptograms