--Originally published at Lord Security
Recently, there has been seeing in the news that the information facebook gathers of its users has been used by private companies, like Cambridge Analytica, more specifically in the use of information for electoral purposes in many countries, like USA.

After that scandal, Facebook has been the center of the atenttion on all the media, because Facebook’s users has realized all the information it keeps from them. if you would like to know all they have about you, it is posible to download that data.
Steps:
First you go to the drop-down menu at the rightest part of the navigation bar and select settings.

It will open the General Account Settings, where below the account info you can find a link to download a copy of your facebook data.

It will take some time to download a kind of heavy zip file with the data. After downloading it, it’s time to extract it and see all they have about you.


If you would like to go a little step further you can check de script by Dylan Mckay on Ruby to collect phone statitics from your facebook user data. To use this script you need Ruby 2.1 or greater and the Nokogiri library.
To run the script you put in in your facebook folder alongside hrml, messages, and photos folder and run ruby facebook-contact-info-summary.rb

In my case I am glad I didn’t give the permissions in my cellphone, but it is interesting to look at all the could get from me if I had.
References: https://gist.github.com/dylanmckay/2b191a10068bd87d0fffba242db44b52














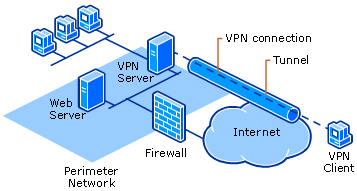


 Here’s a website claiming which are the top 5 VPNs: http://top5-vpn.com/hp-id-2/?gclid=CjwKCAiAtorUBRBnEiwAfcp_Yzhx0VZrS3fABj3i8hYXMzgf_q6SHw9-WNUm_BEtsx1Zh239O0M9EBoC_IoQAvD_BwE
Here’s a website claiming which are the top 5 VPNs: http://top5-vpn.com/hp-id-2/?gclid=CjwKCAiAtorUBRBnEiwAfcp_Yzhx0VZrS3fABj3i8hYXMzgf_q6SHw9-WNUm_BEtsx1Zh239O0M9EBoC_IoQAvD_BwE