--Originally published at Computer and Information Security
Hello reader! Is nice to know that you keep looking at my posts. This time I will talk about the AIC (Availability, Integrity and Confidentiality, some sites or information around the globe refers to this as CIA, yes like the Central of Intelligence Agency in the USA, but this has nothing to do with that).
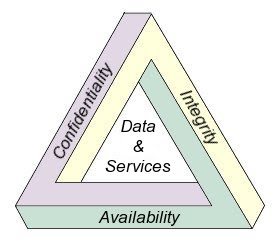
Formally this is how most IT security practices are ruled, this three words are the fundamentals of security, let me explain to you what each one means:
- Availability: Everything should be up and running, no matter what happens, the service or system should always respond.
- Integrity: Nothing can be altered in terms of the information that is used in the service or system without detection.
- Confidentiality: All information or data used should never be shared with third or unauthorized parties, since all of that is personal and literally confidential.
This three concepts are commonly applied into databases, since all information and data processing is stored by a company, so, you reader, are always in touch with this concepts everyday, because is possible that you use an app or something in the cloud that involves data sharing, text messaging or anything were you have to upload something to the network and read or download something from someone else, for example, whatsapp, e-mail, facebook, twitter and many more. Therefore, when you accept the privacy and security conditions (those little letters that pop up in a window where you click accept), you are accepting his own AIC rules, but obviously, they are regulated by a certification, they can’t fully change them for their benefit, because, this rules are made to benefit the user or customer. And that’s why you should always read this bunch of words in a small window.
Going back to the AIC Triad, if