--Originally published at Computer and Information Security
Author: cande123gut
Classic Security Architecture Models
--Originally published at Computer and Information Security
Howdy once again reader! Today’s topic is about some basic architecure models to give security in a system.
Security models of control are used to determine how security will be implemented, what subjects can access the system, and what objects they will have access to. Simply stated, they are a way to formalize security policy. Security models of control are typically implemented by enforcing integrity, confidentiality, or other controls. Keep in mind that each of these models lays out broad guidelines and is not specific in nature. It is up to the developer to decide how these models will be used and integrated into specific designs.
The most frequented or used are:
Lattice
A lattice is a mathematical construction with:
- a set of elements
- a partial ordering relation
- the property that any two elements must have unique least upper bound and greatest lower bound
A security lattice model combines multilevel and multilateral security.
Lattice elements are security labels that consist of a security level and set of categories
State Machine
In state machine model, the state of a machine is captured in order to verify the security of a system.
The model is used to describe the behavior of a system to different inputs. It provides mathematical constructs that represents sets (subjects, objects) and sequences. When an object accepts an input , this modifies a state variable thus transiting to a different state.
Implementation tips:
- The developer must define what and where the state variables are.
- The developer must define a secure state for each state variable.
- Define and identify the allowable state transition functions.
- The state transition function should be tested to verify that the overall m/c state will not compromise and the integrity of the system is maintained.
Noninterference
The model ensures that any actions that take place
Security on the Web (User Perspective)
--Originally published at Computer and Information Security
OMG! Reader, you keep looking at my posts, I’m so flattered. This time I will talk about how you can prevent get in to the wrong website.
The first thing that you should check, when you visit a website, no matter what type of website, but please, if you need to visit a payment website is really important that you first check their SSL certficate, I think nowadays Chrome tells you when a website is not secure. So, once the browser tells you that the browser is not secure, immediately leave it and don’t type or click in anything, you don’t know that scripts or dirty code lives there.

Another recommendation of how you can avoid this is by visiting official pages, if you want to buy tickets for a concert and you know that a certain retailer has a valid webpage to buy them, then buy them there, don’t trust those website that post something cheaper, only because is in their website, that doesn’t guarantee it is true.
 This is not a sponsored post, just as an example of an official retailer
This is not a sponsored post, just as an example of an official retailer
One more advice I can give you is that never click those nonestop ads in any webpage, you could get into a website that could officialy infect you computer with stuff downloaded. With a simple click, your computer could be finished.

That’s it folks, see you in the next post!
References:
So you want to know about Bitcoin…
--Originally published at Computer and Information Security
Hey reader! I’m glad you keep digging at my posts, that’s nice of you. This time I will talk about Bitcoin.
From the official page of Bitcoin we can find that this type of coin is:
Bitcoin uses peer-to-peer technology to operate with no central authority or banks; managing transactions and the issuing of bitcoins is carried out collectively by the network. Bitcoin is open-source; its design is public, nobody owns or controls Bitcoin and everyone can take part. Through many of its unique properties, Bitcoin allows exciting uses that could not be covered by any previous payment system.
As you can see, the P2P technology that they talk about is something called blockchain, which you can read about in my previous post. In the big picture, Bitcoin is nothing than just a program that uses hash tables and is about transactions made in the web through a certain amount of time, and the one that solves the math problem first is the one that can charge a small amount of the bitcoin value.
That’s it, I tryied to explain to you in simple words what this is, but as I know that you are more graphical than just words, I will leave a video of how to create your own Cryptocurrency in JavaScript:
Part 1
Part 2
References:
Blockchain – As you saw it on TV! Actually in the web with Bitcoin
--Originally published at Computer and Information Security
Sup, reader! I feel like a little rusty talking to you since I haven’t uploaded in a while and that’s something I want to change today.
Today’s topic is about blockchain, you will be asking yourself, wt… is blockchain, well, this is nothing that how Bitcoin works, I mean, this is not a post about Bitcoins if that’s what you think you will learn here, for that I recommend you to look it up in my later blog post, where I talk about some cryptocurrency. But, for now I will explain as how I understood from a video that a person made online. I will tell you how I interpret it, but of course I will leave the video down somewhere here, for you to understand the basic concepts about how something like Bitcoins work.
First we have an ecosystem of computers connected in the whole world, through the internet, imagine like a bunch of computers connected with a lan, something, like a mesh. For example this image:

Here you can see a lot of devices connected, this is known as a descentralized and distrubuted, distributed because, each computer or device has a copy of each transaction and doesn’t depend on a third party, like how banks works, where you need a banc account which is managed by a banker and in order to reflect when you make a transaction, it needs to be aproved by this banker. So, in blockchain, what is trying to do, is to remove those third party entities, so that, each one of us can have a very transparent and out of corruption system. And, descentralized because, the transcations are reflected in each device connected to this system.
The basic component of the blockchain is a layer, which is something like you see in the
Hacking adventures (Story 2)
--Originally published at Computer and Information Security
Yo, reader! I’m glad you keep an eye in my blog. Today’s story, is about the new GeForce Now service from Nvidia, which is only available currently for mac users since it is in beta. In this service you can log in to one of their virtual computers on the cloud, to be able to play video games through your steam account.
I tested this new gaming service and I can say that this is a pretty good way to play. Before Nvidia launched this, there was another one called OnLive, the Netflix for gaming, you were able to rent a game for a certain amount of time or even buy it, but it was a copy of the game and it was never yours. It used their self-made interface, it means that I couldn’t see anything but just what they allowed me to see with their own design. Which was identical to the windows tablet or phone theme, like squares or windows. A long time ago I tested this service, I was most of the time logged in and playing games since I couldn’t afford a gaming PC and when they closed it, like around 3 years ago, I got really sad. Anyways, when I heard about Geforce Now I remembered the old times in OnLive, but this time it was different, the gaming process was through your steam account and not by renting or buying the game through a custom menu, it was actually a windows 10 virtual machine. As you know, I’m a pretty curious person, therefore I decided to click anywhere to check if I could get into the desktop menu, but as you already know, everything was locked up. But I never gave up, actually I managed to install chrome, through the internet explorer
Crypto… what?
--Originally published at Computer and Information Security
Hey reader! Welcome once again to my blog, is good to have you here. Today I will talk about cryptography. Cryptography is a method of storing and transmitting data in a particular form so that only those for whom it is intended can read and process it.
You might have an idea about cryptography, since you have watched the Davinci’s code or have seen the egypcians hieroglyphics. The word is derived from the Greek kryptos, meaning hidden. The origin of cryptography is usually dated from about 2000 BC, with the Egyptian practice of hieroglyphics. These consisted of complex pictograms, the full meaning of which was only known to an elite few. The first known use of a modern cipher was by Julius Caesar (100 BC to 44 BC), who did not trust his messengers when communicating with his governors and officers. For this reason, he created a system in which each character in his messages was replaced by a character three positions ahead of it in the Roman alphabet.
But let’s explain this in computing science terms. The meaning and functionality is the same, it consists of hidding or cover a message so that only the reader with a valid key can descypher the message and read it, the computing science stuff gets involved in the process of how the message is encrypted and how to generate a key to share it with someone.
Modern cryptography concerns itself with the following four objectives:
- Confidentiality: The information cannot be understood by anyone for whom it was unintended.
- Integrity: The information cannot be altered in storage or transit between sender and intended receiver without the alteration being detected.
- Non-repudiation The creator/sender of the information cannot deny at a later stage his or her intentions in the creation or transmission of the information.
- Authentication: The Continue reading "Crypto… what?"

Hacking adventures (Story 1)
--Originally published at Computer and Information Security
Oh! Hi reader, I’m really impressed that you keep coming to read what I have to tell to the world hehehe. This time I will tell a little story as I promised on my first post.
It all begins when I was in highschool, the really young and naive Cande, the little geek who was starting to learn how to set-up a web site server. One day, Cande got an idea, he thought: “What if I set-up a CMS in my brother’s server to learn how a server works and how to manage files in there, but also to share some of my thoughts to the world?” Well that sounds really cool isn’t it? You might think, oh wow this guy has some initiative, but in that time, he also had a lot of naivety. Let me explain to you why:
- He downloaded a wordpress template from those sketchy sites that offer everything free to download, he thought: “Oh, I’m going to search a cool wordpress template and modify it to make it look nicer!”
- After he downloaded it, he made all the modifications in his machine: “Where is the style folder of this template? Oh I found it!” -2 hours later-, “Cool, I finished my master piece”.
- Then, he opted to upload all of his downloaded files to the server: “Ok, now I just need to upload my root folder to the server.
- Once his site was uploaded, he went to check it, to see if everything was ok: “Everyhting is up and running, now, I just have to enter my site address and check it out, I’m really excited” -1 minute later-, “Hell yeah, my site rocks, looks pretty cool, I’m gonna start publishing my first post”.
- Days passed and each day Cande logged in Continue reading "Hacking adventures (Story 1)"

How to prevent e-mail viruses?
--Originally published at Computer and Information Security
Hello reader, today’s topic is about e-mail viruses. We all have been in the wrong position where you download a file or something sent through the mail, and never check if the sender is a real one or check if the file has a proper extension depending on the type of file you were supposed to receive (For example: a text file should end in .txt a pdf in .pdf, etc.) but many people doesn’t check about that and just double click the downloaded file, which ends in another zombie computer infected with viruses like trojans or worms, which keep reproducing and propagating through the home or any network to other devices.
So, in order to at least prevent that you get infected with any virus, you first should evaluate the mail sender, check if the mail that is sending you a mail is valid and track it. So, I recommend you to use this tool, in order to check an e-mail:
https://tools.verifyemailaddress.io/
It gives you metadata (important and detailed information) of the e-mail, that tells you from where it was sent, servers, validation of the records and a score of reputation.
For example, here is the score it gave me of some mails and data from the server of the fake account:
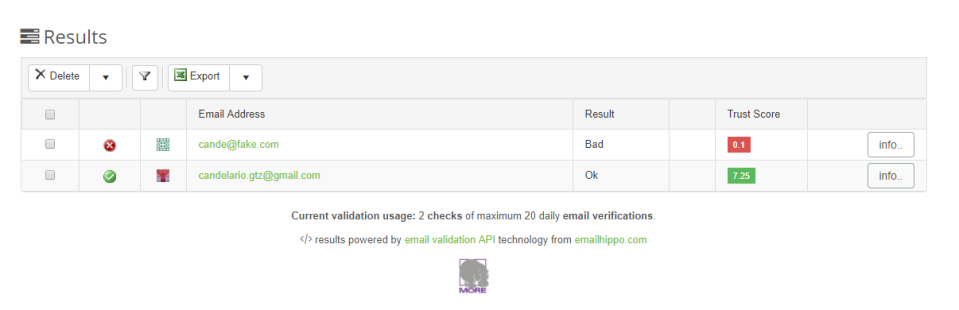
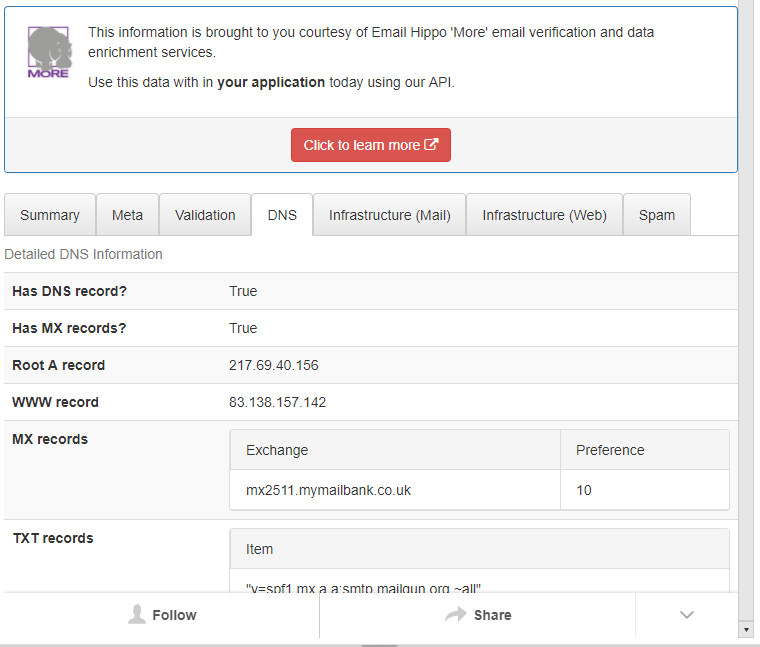
After you check a mail validation and the score is almost trustworthy, you should Google the e-mail addres to re-validate.
And one last thing, never, ever, click links inside a mail. If your guts tell you that it might be a phising or a scam, it is probably one.
See you on the next post!!!
WT… is Denial of Service?
--Originally published at Computer and Information Security
Hi reader! I hope you are enjoying my posts, this time I am going to talk about DoS (Denial of Service). So, in simple words, this is a common and most used technique by hackers and people that want to see the world burn, it occurs when an attacker takes action that prevents legitimate users from accessing targeted computer systems, devices or other network resources.
This type of attacks usually send a lot of information, data or traffic to a server, through a bunch of other helpers called zombies, in order to staturate the network in that server or victim resources and make it impossible for the victim to use the service properly.
Some characteriztics of this attack are:
- Degradation in network performance, especially when attempting to open files stored on the network or accessing websites.
- Inability to reach a particular website.
- Difficulty in accessing any website.
- A higher than usual volume of spam e-mail.
- Hard to play a videogame since there is a lot of lag or traffic from the nework.

To restore the normal use of the service in those cases, a reboot of the system fixes the DoS attack, but there are a lot of different types of this attack that can more difficult to recover from:
- Buffer overflow attack: Is a catchall description most commonly applied to DoS attacks that send more traffic to a network resource than was ever anticipated by the developers who designed the resource. One example of such an attack sent, as email attachments, files that have 256-character file names to recipients using Netscape or Microsoft email clients; the longer-than-anticipated file names were sufficient to crash those applications.
- DDoS attack: The attacker may use computers or other network-connected devices that have been infected by malware and made part of a botnet. Distributed denial-of-service attacks, especially those using botnets, use command-and-control (C&C) Continue reading "WT… is Denial of Service?"