--Originally published at TC2027 – Surviving CS
What is encryption?
Encryption enhances the security of messages or files because only those who have the right key can open the message and read it. This type of security dates back a long time from Julius Caesar to the Nazis, the need to hide or protect our information to stop people other than its intended recipient from reading it.
So to start encrypting a message you need a key to start an encryption and also you need a key to decrypt the message. If someone is listening and hijacks the message he/she can’t read it because they don’t have the proper keys to unlock the message.
There are two methods to encrypt data:
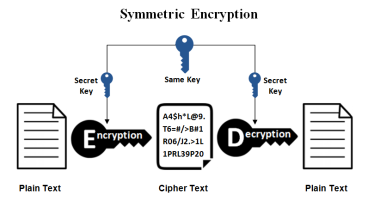
- Symmetrical encryption – In this type of encryption both the sender and the receiver need to have the same key in order to make an encryption or decryption.
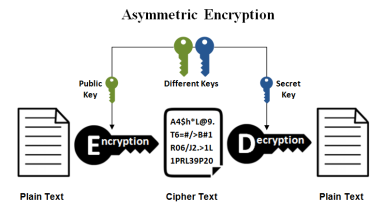
- Asymmetrical encryption – In this type of encryption has two keys one public and one private, they public key is available to anyone who wants to send you a message but the private key only the receiver has it, this way only the owner of that private key can decrypt the message.
Source:
https://www.ssl2buy.com/wiki/symmetric-vs-asymmetric-encryption-what-are-differences
