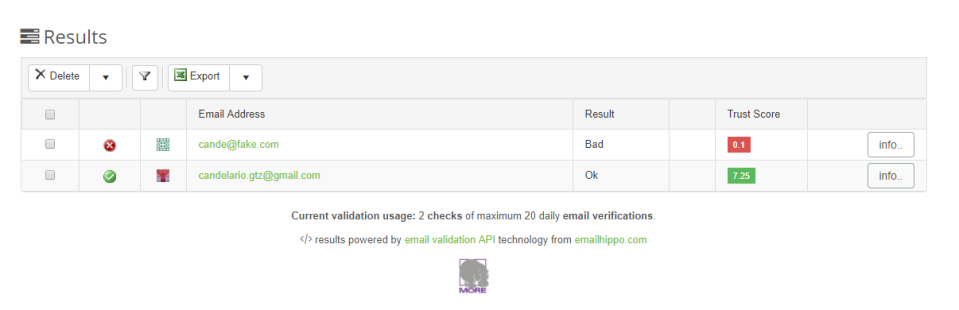
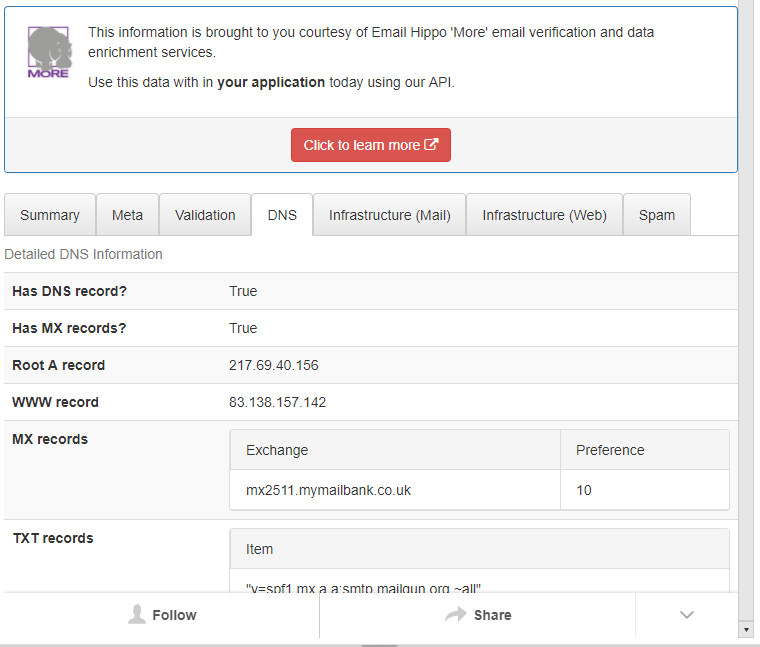
--Originally published at Computer and Information Security
Hey reader! I’m glad you keep digging at my posts, that’s nice of you. This time I will talk about Bitcoin.
From the official page of Bitcoin we can find that this type of coin is:
Bitcoin uses peer-to-peer technology to operate with no central authority or banks; managing transactions and the issuing of bitcoins is carried out collectively by the network. Bitcoin is open-source; its design is public, nobody owns or controls Bitcoin and everyone can take part. Through many of its unique properties, Bitcoin allows exciting uses that could not be covered by any previous payment system.
As you can see, the P2P technology that they talk about is something called blockchain, which you can read about in my previous post. In the big picture, Bitcoin is nothing than just a program that uses hash tables and is about transactions made in the web through a certain amount of time, and the one that solves the math problem first is the one that can charge a small amount of the bitcoin value.
That’s it, I tryied to explain to you in simple words what this is, but as I know that you are more graphical than just words, I will leave a video of how to create your own Cryptocurrency in JavaScript:
Part 1
Part 2
References: