--Originally published at TC2027 – Will It Blog?
Everyone has heard of this term at some point. Whenever a program installed in your computer doesn’t work, one of the first “recommendation” or quick solution is to turn off the firewall. This is super risky because the firewall is the first line of defense an OS has.
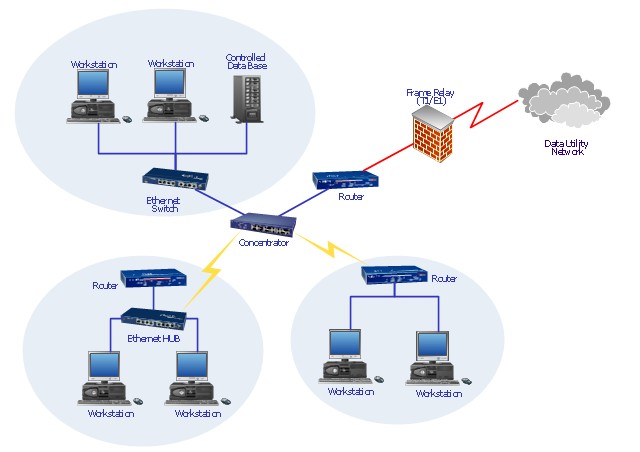
Firewalls stands between the computer or networks in which the machine resides, and shields it from the dangers on the internet. Sometimes it is also referred as a Containment device.There are two kinds of firewall: it can either be a software program running on a computer or it can be build into a hardware device such as a wireless base station or a router hub (like the one below).
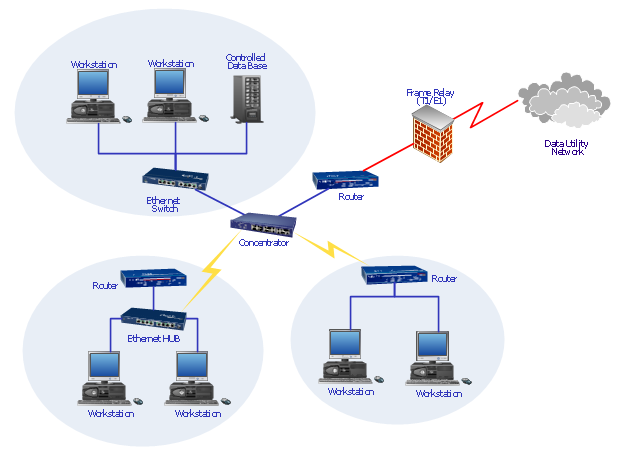
The way a firewall works is by dividing the network in various zones and regulating the activity inside it. This is basically just avoiding the issue with non-authorized traffic so it can not enter or leave a certain zone. Even more concise a firewall lets you take control of the flow of data.
But a firewalls functionality doesn’t just limits itself to block access to non-authorized packets. It has two mayor roles: prevent and detect.
Prevents in the way that it filters the traffic in accordance to a security directive. Common filtering criteria comes from the following:
- IP address
- Type of service
- Port number
- Header Data
Firewall also detects attacks. It registers the accessing hosts or network attempts and it alerts administrators when the attempts look suspicious of being an attack.
How is it done?
Discarding Pings
This uses one of the most basic network tools used in order to see if a certain host is up and running, the PING !
Ping Utility: sends data packets to the remote system represented by its ip address and waits for a reply
There is


Packet Filtering
To make it brief the traffic on a network is labeled with a pair of IP addresses, that indicate the source and destinations of the packages.NOW the traffic in a network that involves the use and access to a certain service (TCP = 23 , HTTP = 80, SSH = 22.. and others) is labeled also with a port. This (IP add. and port) together identify the service on a specific machine. This way the firewall can block traffic coming from an IP address.
Port Forwarding and blocking
As mentioned earlier systems need ports in order to communicate. Firewalls can also be used to block entire ports that the system doesnt require to be open. Port forwarding is telling your firewall who has permission to use a port, lets say your are outside the network and want to use telnet which uses port 23, you can configure in advance the firewall to ‘forward’ packets coming from your address outside the network in order to perform telnet.