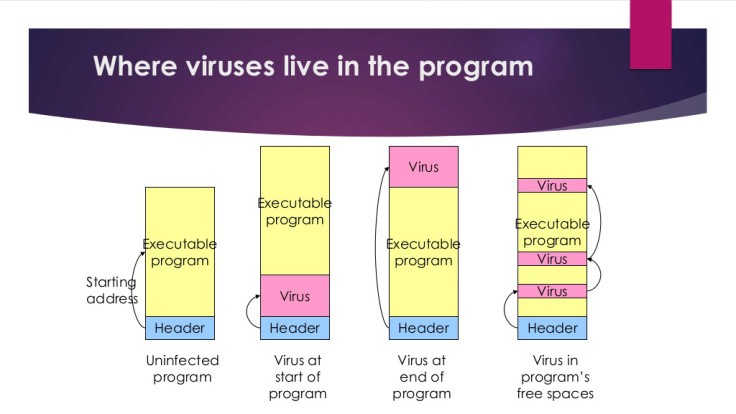
--Originally published at The shield of the world
So when we talk about Computer Security there is a topic that some of us really think about. How to ensure the ethical and legal responsibilities, why this? Because when someone has the knowledge about this topic is easy to go from white to black hat in a matter of seconds.

There are some other professionals whose jobs duties affect others’ lives and they receive a formal training, to address ethical issues and how to deal with them. In the case of the IT security personnel they have access to confidential data and knowledge about individuals’ and companies’ networks and systems that give them a great deal of power. That power can be abused, either deliberately or inadvertently. But there are no standardized training requirements for hanging out your shingle as an IT pros are beginning to address the ethical side of the job, but again, there is no requirement for IT security personnel to belong to those organizations.

This is something related to what happened to Tec de Monterrey, when the institution was growing and becoming important in the country as a quality education institution, their mission was to deliver a god tier prepared technicians to the professional world. And they did, but they all lack of ethical values and were some of the critics that the institution received as feedback from the enterprises that hire the graduates from Tec.
Nowadays the institution has more courses related to ethical challenges and how to deal with them, debating about the best solution with a global perspective of the affected ones. As a technical related career we, with the help of the professors are developing an ethical guidelines. Is something when everybody should be related to.
So the main responsibility is to respect the privacy of the information an IT or