--Originally published at The shield of the world
So we all know that friend who have been so closed to kill his PC, without even knowing. And this is the topic for today, unintentional security issues. This is so common that you probably have already thought about some examples of yourself.
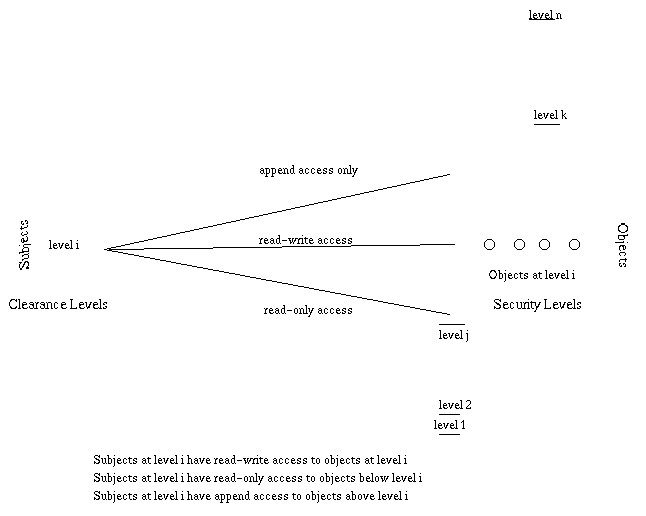
This is one of the most common causes of lost of information in enterprises so we are going to talk about how to prevent them.
- Control applications.- If we control the applications that the users can download and use in the working laptop, we are reducing the probability of an unintentional issue by a really big amount. But is not that easy, because the web browsers and email clients, are the most common points of entry for malware. A good solution for that software that is dangerous is to run it un isolated virtual machines. If the app is malicious, any infections would occur only in the VM and there is no harm to the host operative system.

- Filtering content.- Another solution and kinda related to what Adblock can offer, is filtering bad content. Strategically blocking only a small subset of harmful activity can have positive impact on minimizing the damage from an adversary.
- Limit executable content.- Blocking all files of a certain type, while effective, is not always feasible if the files are needed by the user. Effective technology exists that can take an attachment, perform analysis of the content, and even run it in a sandbox to examine the behavior; if it is malicious, it would be blocked, and if it is legitimate, it is allowed through. This gives a lot of flexibility, but limits the impact of stopping normal activities.

- Control executable.- Compromising an accidental insider is usually done by tricking the user into running an executable that they believe

 Continue reading "Is not my fault!"
Continue reading "Is not my fault!"