--Originally published at Miss F.
This week I decided to sneak in to a digital identity course that’s being taught by my security teacher Ken Bauer. My reasons behind this were to basically know what “regular” people (by this I mean non-tech savvy people) are afraid of, what their doubts about the internet are and the reasons why they don’t feel safe online. This will give me a better perspective on what to talk about in this blog and how to talk about it.
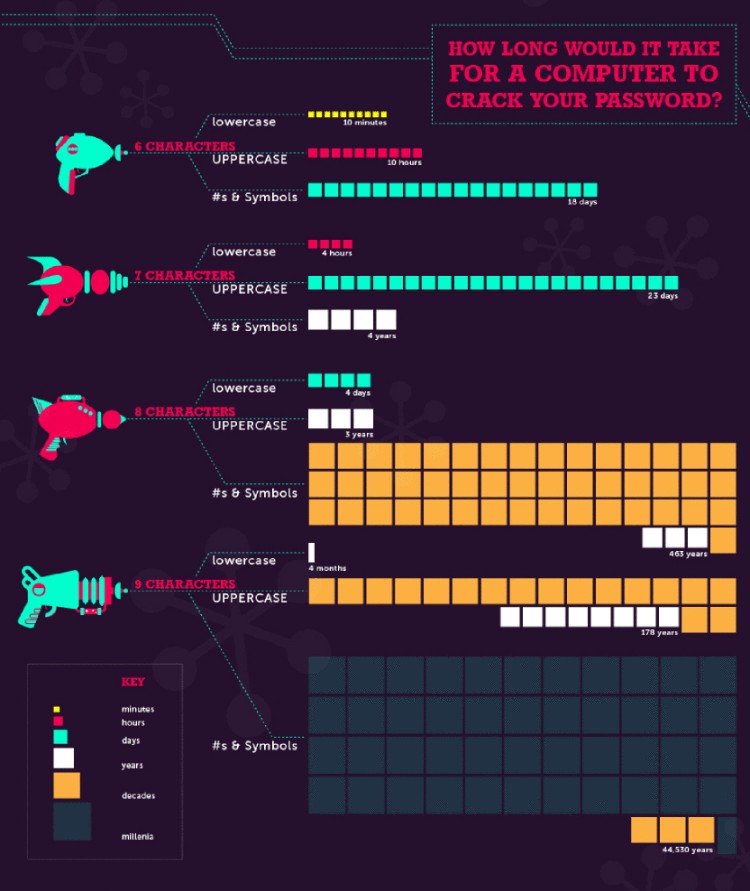
Today’s day one and I’m writing this as we take the course, so I’ll talk a bit about the experience. We had a talk with Dave Cormier and people dared to ask several questions. Interestingly enough, all the questions so far have been completely related to security. Will hackers get me? Is my information safe? What do people generally steal from internet users? Will I ever get hacked?

The answer to all of this was: you are always at risk.
Since the course is about digital identity, I will also talk about that. First of all, what is digital identity? It’s basically the way you represent yourself online. It’s how people will see you on social media. You may think “but it’s the internet, I can be whomever I want to be!” to that I say, of course you can! However be ready to face the consequences of that. Digital identity is similar to a tattoo. You choose the design and ink it in your body forever and ever. So, like a tattoo, be sure to create something you like, something that represents you and preferably something you aren’t ashamed of.

Once you realize everything you do can be found by literally anyone, you can start worrying about all those terrible, terrible pictures from middle school. That bad hairdo will be