--Originally published at Don't Trust Humans, Trust Computers
We live in an era, where everybody has some kind of digital device. Most of us have at least 2 of this devices, if not more. We interact with them in a daily basis; in our work, in our home, at the school, at entertainment centers, etc. This gadgets are taking over the world, but most importantly our lives. And if this devices are being an essential part of our lives, well… we are very likely to have some security threats on our way. In our lives, we are always expose to some kind of threat, even if we like it or not, and if we have a digital device, we are expose to a different new kind of threat, that it didn’t exist before.

There exist so many cyber security threats out in the world, and we need to be prepared if we encounter one. So here I am going to list you some of the most common threats and some countermeasures to those problems.
- Spoofing user identity.- using a fake authentication to gain access to a system.
- Countermeasures:
- Do not store passwords in files.
- Use a strong authentication.
- Do not send passwords over the internet.
- Countermeasures:
- Tampering with Data.- unauthorized modification of data.
- Countermeasures:
- Use digital signatures.
- Use data hashing and signing.
- Use strong authentication.
- Countermeasures:
- Information Disclosure.- unwanted exposure of data.
- Countermeasures:
- Use strong encryption.
- Use strong authentication.
- Countermeasures:
- Phishing.- making use of a fake email or webpage so user can put personal information
- Countermeasures:
- Delete suspicious email.
- Enter to verify websites.
- Look for digital signatures.
- Countermeasures:
- Malicious Code.- software that cause malfunctions inside a system.
- Countermeasures:
- Turn off automatic downloading.
- Block malicious websites.
- Stay current with OS updates.
- Countermeasures:
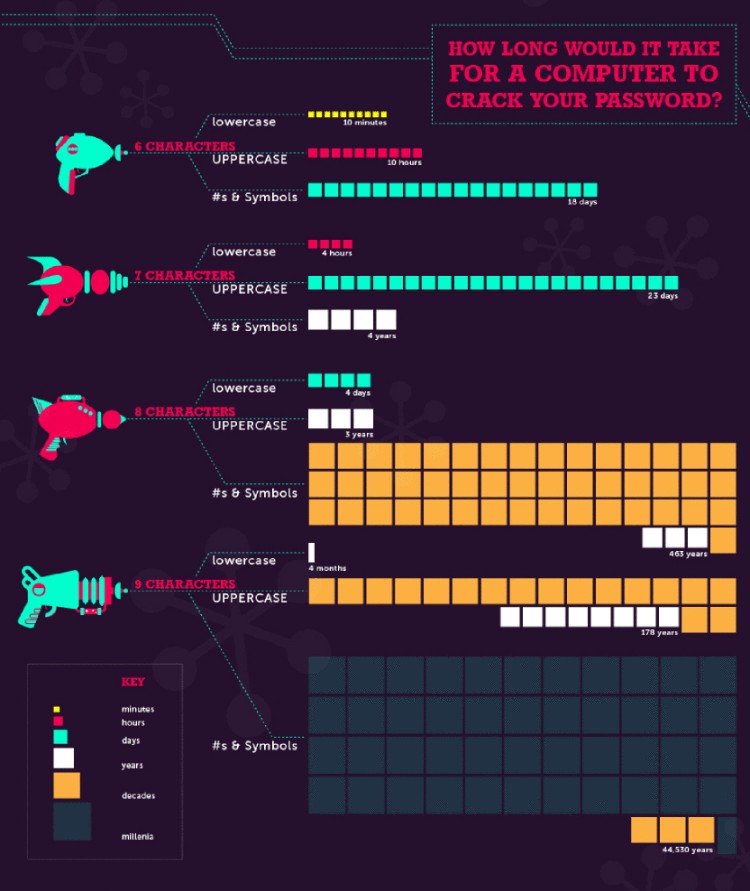
- Weak and Default Passwords
- Countermeasures:
- Combine letters, number and special characters.
- Don’t share your password.
- Don’t use
 Continue reading "Security Countermeasures"
Continue reading "Security Countermeasures"
- Countermeasures: