--Originally published at TC2027 – Will It Blog?
Yesterday on a workshop about a rapid prototyping tool for making web applications, a classmate asked about the options that the tool offered in order to authenticate users. For that the instructor went along to ask us if we knew the difference between authentication and authorization.
An easy way to differentiate both is to make two questions. Who’s allowed to log in? (authentication) and once the user is already logged into the system, what is he allowed to do? (authorization). That just comes as an introduction in order to talk about the different types of authentication that exist out there, it is not important to remember all of them exactly but if you can read them once you will know what can be done in order to accomplish a reliable authentication method.
In most kind of systems you identify yourself with some kind of identifier (usernames, emails) followed by a password, that is the most common authentication method and it is called PAP (Pen Apple Pen, just kidding it stands for Password Authentication Protocol). At the most basic level you will have the server looking for these values on the tables and if there exists a record then grant access.
Challenge Handshake Authentication Protocol (CHAP)
In this method the server in charge of the authentication process sends the user an ID and a random number, also the sender and receiving program share a predefined secret word.
So the client strings together ID + generated random + secret word, in order to make a key that can be hashed, this retrieves a new value. This new value is sent to the authenticator, which now has the job to compare it with a built string made by itself using the same hash.
Mutual Authentication
Also known as two way-authentication.

One-time Password (OTP)
This is a simple yet clever one that can be an option to PAP, so if you are still deciding in an authentication method with minimum complication at least use OTP. With OTP the user creates a password and internally the system creates a variation of the password each time a password is required, so no password is ever used twice. Useful against snooping.
Per-session Authentication
This is a tedious one that requires the client to re authenticate for each exchange of information. I don’t know if you have deleted a repository on github but If you go and do it it will ask you to re authenticate yourself even if you are already authenticated. It can be annoying but it provides great deal of security, against snooping
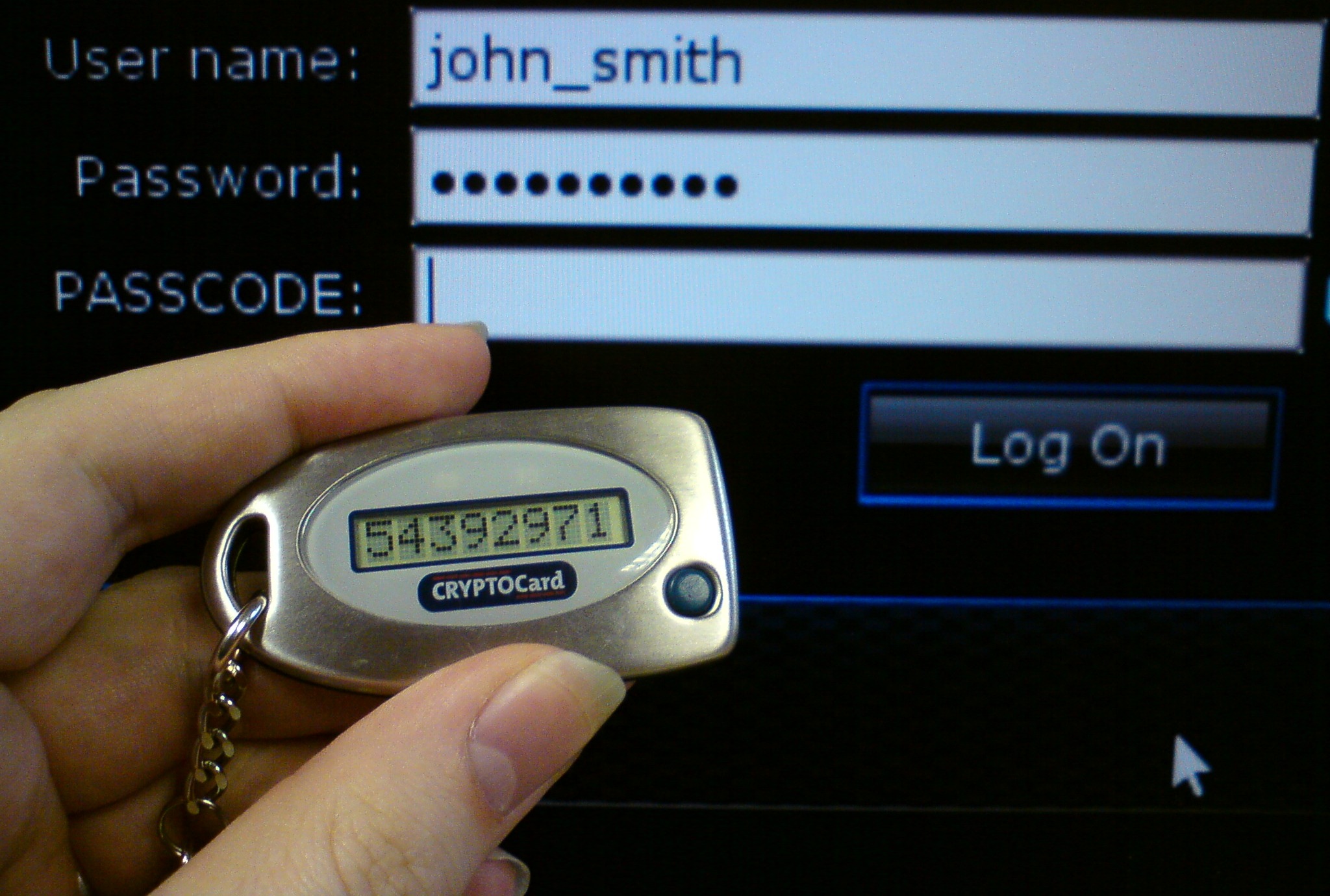
Token Based
A token or token card is presented as a small hardware device (like the one on the image) that supplies a response to a certain input that the server challenges to the device. You might call it outdated but it is also a valid method to authenticate. There is a different kind of token called access token users enter their username and password in exchange the user gets a token encapsulating his identity in order to fetch a certain resource for a limited time (yes they might expire). The user can offer the token to the site via post, get or a cookie to obtain access to data inside the site this way the user authenticates himself.
Token based authentication has become very popular nowadays, here are some of the good aspects that come when we use tokens:
- Portability, that’s how I’m calling it, but what I mean is that it can be supported in multiple platforms. Resources are available from any domain in any kind of device as long as the token is valid.
- States, token data can hold up the information of the current state of the user session.
- Security (U don’t say). Tokens being able to expire and not sent directly to the server via cookies make it secure.
Several api’s offer this kind of authentication, the only one that I have seen working is Firebase api. In my experience, just in the front-end on a simple log in you would use the api to request data using the username a password fields, also you request which data you are going to consume for that user.
There are other types of authentications like biometrics, (fingerprint, voice) remote access and others. And the post went too long so I’ll be talking about Access Control Methods on another one.
Information comes from:
https://scotch.io/tutorials/the-ins-and-outs-of-token-based-authentication
https://www.w3.org/2001/sw/Europe/events/foaf-galway/papers/fp/token%5Fbased%5Fauthentication/



