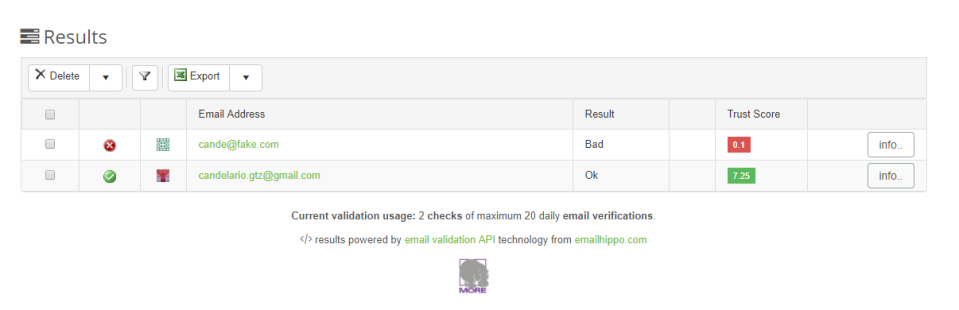
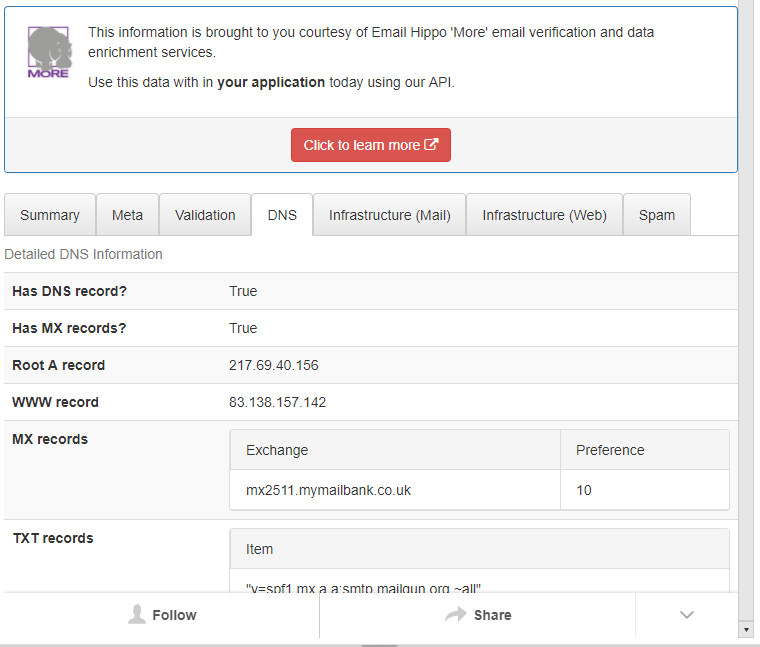
--Originally published at Computer and Information Security
Oh! Hi reader, I’m really impressed that you keep coming to read what I have to tell to the world hehehe. This time I will tell a little story as I promised on my first post.
It all begins when I was in highschool, the really young and naive Cande, the little geek who was starting to learn how to set-up a web site server. One day, Cande got an idea, he thought: “What if I set-up a CMS in my brother’s server to learn how a server works and how to manage files in there, but also to share some of my thoughts to the world?” Well that sounds really cool isn’t it? You might think, oh wow this guy has some initiative, but in that time, he also had a lot of naivety. Let me explain to you why:
- He downloaded a wordpress template from those sketchy sites that offer everything free to download, he thought: “Oh, I’m going to search a cool wordpress template and modify it to make it look nicer!”
- After he downloaded it, he made all the modifications in his machine: “Where is the style folder of this template? Oh I found it!” -2 hours later-, “Cool, I finished my master piece”.
- Then, he opted to upload all of his downloaded files to the server: “Ok, now I just need to upload my root folder to the server.
- Once his site was uploaded, he went to check it, to see if everything was ok: “Everyhting is up and running, now, I just have to enter my site address and check it out, I’m really excited” -1 minute later-, “Hell yeah, my site rocks, looks pretty cool, I’m gonna start publishing my first post”.
- Days passed and each day Cande logged in Continue reading "Hacking adventures (Story 1)"