--Originally published at Computer and Information Security
An important requirement of any information system is to protect information against improper disclosure or modification. To achieve this goal authentication and access control technologies are used.
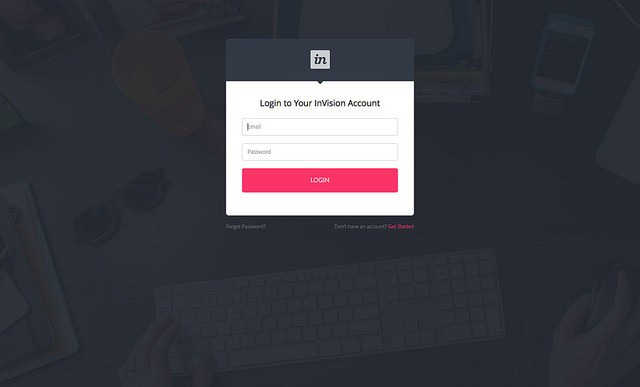
Authentication establishes the identity of a user to the system before access is granted. This is typically done by means of an user name and a password.
Access control constrains what a user can do. Access control consults an authorization database in order to determine if the user attempting to do an operation is actually authorized to perform it.
Photo by:
Flickr photo by Gustavo da Cunha Pimenta https://www.flickr.com/photos/guspim/16068339396/ shared under a Creative Commons (BY) license

