--Originally published at Mental Droppings of a Tired Student
Last week (I know I’m pretty behind in writing this post), we had a couple of encryption activities in class. We were asked to code, in the language of our choice, a program to encrypt a text file using the Caesar Cipher as well as the Vigenère Cipher (user input of the text file and key).
Despite dehydration and tiredness, I was able to produce some code in C for the Caesar Cipher.
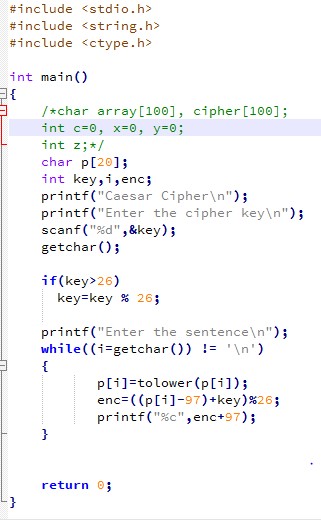
This was just a quick program that encrypts your message. After that I cleaned it up and made several functions, including the decryption function.

This little web widget was useful to check if my code was encrypting and decrypting correctly.
For Vigenère Cipher I consulted this video to figure out how this encryption works:
I somehow decided to switch to java, it seemed easier for me at the time. I made this during class… It’s a function to get the number of shifts you’ll be cycling through. After that I went to get something to eat because I was starving, by the time I got back class ended so I didn’t get to finish.

According to the video, for the word “math” you would have 12 shifts for “m”, 0 shifts for “a”, 19 for “t” and 7 for “h”. My code yields:
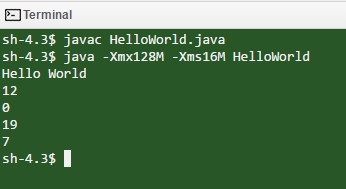
So I was on the right track, but it’s pretty safe to say this isn’t the most efficient code. So that weekend I changed it completely, and decided to stick to c to make everything uniform and simpler.

This webpage helped me check my code.
I uploaded my code to GitHub, take a look at my repository here.
I also happen to be behind on other activities regarding the encryption topic. It’s that time in the semester when you can’t seem to get your sh** together, so bear with



Here is an encrypted message for Ken, using keybase.
What is public key encryption/cryptography ?
In 1976, Whitfield Diffe and Martin Hellman created public key cryptography. Public key cryptography represents a major innovation because it fundamentally alters the process of encryption and decryption.Instead of a single shared, secret key, Diffe and Hellman proposed the use of two keys.
One key, called the “private key” remains a secret. Instead of being shared between parties, it is held by only one party. The second key, called the “public key,” is not a secret and can be shared widely. These two keys, or “key pair” as they are called, are used together in encryption and decryption operations. The key pair has a special, reciprocal relationship so that each key can only be used in conjunction with the other key in the pair.
The key pairs are mathematically related to one another such that using the key pair together achieves the same result as using a symmetrical key twice. The keys must be used together: each individual key cannot be used to undo its own operation. This means that the operation of each individual key is a one-way operation: a key cannot be used to reverse its operation.
In addition, the algorithms used by both keys are designed so that a key cannot be used to determine the opposite key in the pair. Thus, the private key cannot be determined from the public key. The mathematics that makes key pairs possible, however, contributes to one disadvantage of key pairs as opposed to symmetric keys. The algorithms used must be strong enough to make it impossible for people to use the known public key to decrypt information that has been encrypted with it through brute force.
As long as the private key remains secret, the public key can be given to any number of people and used securely. The ability to use a single key pair with many people represents a major breakthrough in cryptography because it makes cryptography substantially more usable by significantly lowering the key management requirements. A user can share one key pair with any number of people rather than having to establish a single secret key with each person.
Encrypting a directory using encfs
*Pending
References:
https://technet.microsoft.com/en-us/library/aa998077(v=exchg.65).aspx


