--Originally published at Mental Droppings of a Tired Student
Since last week Denial of Service attacks was suddenly “a thing” in most media outlets, I thought it was good timing to drop this mastery post related to the topic.
Unless you are living under a rock you heard about the attacks beginning in the morning of last Friday (October 21, 2016) and stretching into the afternoon. The attack involved multiple DOS attacks targeting systems operated by DNS provider Dyn. This massive DOS attack shut down major websites across the internet, Dyn was hit by at least three apparently targeted strikes. The affected websites included Twitter, Reddit, GitHub, Amazon, Netflix, Spotify, Runescape… (who even plays that anymore?), amongst others. Dyn confirmed it was under attack the morning of said events.

This was their statement:
“Starting at 11:10 UTC on October 21th-Friday 2016 we began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure. Some customers may experience increased DNS query latency and delayed zone propagation during this time. Updates will be posted as information becomes available.”
We discussed this attack briefly during our Networking class, the professor pointed out how DNS is an obvious target for attack. He also made the point that this kind of thing happens when security is put in the back burner; explaining that engineers generally care about functionality and tend to worry about security later or view security as an added plus. However security, as we’ve learned the hard way, should be just as crucial as functionality.
Dyn claimed the problems were mainly affecting customers on the United States East Coast. I was going to say, I didn’t even feel the attack or witness it firsthand at all. I mainly used cisco’s spark, youtube and facebook, who were not under attack.
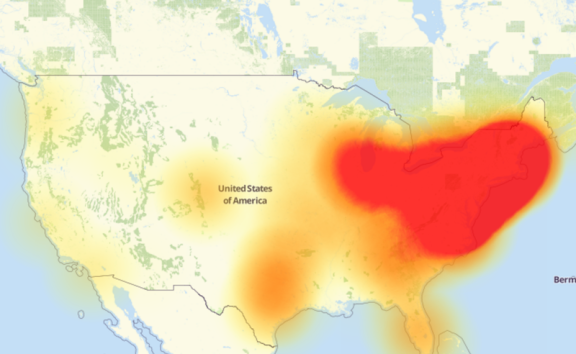


This series of unfortunate events had people wondering what DOS attacks even were, which brought a large group of media outlets giving interesting explanations of their own. I found a decent one, in Business Journal New York, they interviewed Gary Merry, CEO of Baltimore-based cybersecurity company Deep Run Security.

This was his explanation for the general public which I thought was a good one:
“Dyn offers managed DNS and email delivery services to other companies. Essentially, the service works like Yellowpages. When a person types a URL into their browser, a DNS service acts as a middle man. It takes the request and “resolves” it, or directs the user on a path to their desired website.”
“[…] when servers are swarmed, or are fielding millions and millions of the same request — in this case, requests for sites like Twitter or Amazon. The servers go into a kind of “panic.” They are overwhelmed and can’t meet all of the requests at once, so they lock up and stop resolving any requests. And when Dyn servers can’t resolve those requests, users are met with a blank screen instead of the website they’re searching for.”
“So we say Twitter is ‘down.’ But actually Twitter is functioning perfectly well, you just can’t get to it,” Merry said. “Basically, Twitter just doesn’t exist for a while.”
“The attack had to be coordinated to send an enormous amount of requests at once from different points, and could have been aided by millions of servers that people didn’t even know were corrupted. For example, a woman in Florida who opened an email and didn’t realize her computer was affected by that piece of malware, would have no idea that her PC was being used in this kind of assault.”
“There are other services that do essentially the same thing Dyn does with stronger protections against swarm attacks like this, Merry said, but those are often far more expensive for businesses.”
“Unfortunately, in cases like this, the devil’s in the details,” he said. “When you go for a lower-cost option, there isn’t the same amount of protection or as much depth of security. That’s the risk businesses have to weigh.”
I thought this last thing he said was very true, which brings me to my next post. Indeed, “the devil’s in the details” when it comes to security.
References:
http://www.theverge.com/2016/10/21/13357344/ddos-attack-websites-shut-down
https://en.wikipedia.org/wiki/October_2016_Dyn_cyberattack


