--Originally published at The Hitchhiker's Guide to information security… according to me!
Hello and welcome back to the season finale of the Living to the Limit series. I’m your host Edy and I say “Lets Rock!”. (Explosion sound!)

In the previous chapter we discussed about what risk assessment was and the process of obtaining a prioritize list of risks in order to take informed decisions on what to do next. Today we’re going to talk about that next part: Risk Management.
Risk management is the process of analyzing potential responses for each risk and implementing strategies to control those risks. More like an action plan in case something bad happen, and there exist 5 different management strategies.
Avoidance: it’s very literal. It means to get away from the risk itself. For example, walking the long way past home to avoid being hit by bullies. Moving your data center away from the sea to avoid hurricanes.
Transference: just give the problem to someone else. Principally an insurance company or hire a company that trains your personnel to avoid social hacking, etc.
Mitigation: Now this is cool. This is more like dealing with the specific problem approach face to face. If a flood is a risk, building special infrastructure that will make water unable to enter the building will be a good example of mitigation.
Acceptance: the Buddhist approach. You realize you have no money to deal with a specific risk so you just accept that things are the way they are and that you can’t do anything about it. You let it be and pray for the risk to never manifest.
Deterrence: it refers to taking away the determination of a risk to hurt. It doesn’t work with natural disaster, but you can deter a burglar by installing security cameras or buying a guard dog, you’re

Now that you pick up a good strategy for the risk you want to deal with you need to start implementing a security control. Security controls are procedures or mechanisms that are put into place in order to manage risks. Security cameras are a security controls.
There is no limit of how many security control you can implement (except for money, obviously), but a good way of knowing how much security is need is the concept of defense in depth which means that you need to design your control in a way that if one control fails, then there’s another one ready keep protecting. Like locking the door of your home, installing security cameras and buying an insurance.
Security controls are categorized in two areas purpose and mechanism of action.
Purpose controls are categorize as follow.
Preventive: stopping an event from occurring… like your consciousness.
Detective: identifying a potential risk… like your best friend warning you about a girl/boy.
Corrective: dealing with the aftermath of a risk that already happened… like your parents.
Mechanism of action have also 3 categories.
Technical: They use technology to achieve security control objectives.
Operational: this use humans instead of technology to achieve security control.
Management control: this are security controls that use security control to improve security control… wait… what?
Ok, now we have the whole picture of the strategies we can take and the types of security control we can implement, but you know, I would like a step by step guide, for dummies if you may, that tells me a mechanical process of how to manage risks. And luckily for us there are some.
Risk Management Framework
There are several risk management frameworks out there in the big, blue world, but because NIST (National Institute of Standards and Technology) is the most famous one we’ll talk about that one.
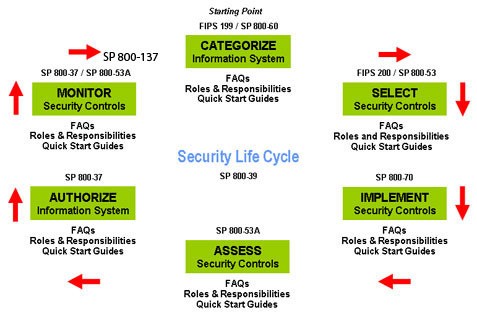
NIST 6 steps process

- Categorize information System: for this step you need to gather information from 2 sets. Architectural information that refers to technical details, models, and system information of the technology in use; and the second set refers to the organization information like business policies, resources availability and supply chain information. After gathering the information you need to do a risk assessment with the information obtained.
- Select security controls: After determining the risk, you need to select the different security control that you might want to use in order to prevent those risks.
- Implement security controls: It’s pretty straight forward.
- Access security controls: after implementing the controls you need to make an assessment about the effectiveness of the control. Are they meeting the objective? Can they be perfected in any way?
- Authorize information system: After all security control are put into place, then the information system can start running.
- Monitor security controls: You need to constantly monitor the efficiency and effectiveness of the security system, and add or remove anything that it’s needed in order to keep the system functioning at its best.
Risk management and risk assessment are cyclical process. You need to be aware of new threats that might damage your information system and design, implement and assess a method for counteract those threats. The life of a security professional is not an easy path but a just one. See you on the next season of the Hitchhiker Guide for Information Security… According to me. Hasta la vista…


