--Originally published at The shield of the world
So let’s start with this…
What is security in OS?
Is when you have issues external to OS and you would ask, why external? Because is the authentication of you, the user, validation of messages, malicious or accidental introduction of flaws, etc. So is not really about the OS.

And what is Protection in OS?
Mechanisms and policies to keep programs and users from accessing or changing stuff they should not do. AND is internal to OS. The OS has to provide this.
So…Protection and Security
An Operating System (OS) is an interface between a computer user and computer hardware. An operating system is a software which performs all the basic tasks like file management, memory management, process management, handling input and output, and controlling peripheral devices such as disk drives and printers. We will call this objects.
And each object has a unique name and can be accesses through a well-defined set of operations.
Protection and security ensure that each object is accessed correctly and only by those processes of authorized users that are allowed to do so.

OS designers faces challenge of creating a protection scheme that cannot be bypasses by any software that may be created in the future.
Networking adds to the problem as it allows access to a computer and its resources without being in the same physical location.

This is the correct way to access and use Resources.
OS have goals like:
- Data confidentiality
- Data integrity
- System availability
And each of this has a threat:
- Exposure of data
- Tampering with data
- Denial of service
One of the solutions is user authentication…you know when you type “password” to actually enter your PC and if you don’t type anything and just has all his information without any little layer of protection should use at least a



If you write both the user name or ID correct and the Password the OS successfully will login.
If things don’t go so well logic will be rejected after name entered and/or login will be rejected after name and incorrect password entered.
The OS should not notify the user if the password is correct or not when is not fully entered.

So security in an OS is more about mechanism of defense of information, devices, etc. and protection is more about specifying policies. How to decide who can access what? Specifications must be correct, efficient and easy to use. A good example is when you have to actually write sudo on linux terminal to make some action.

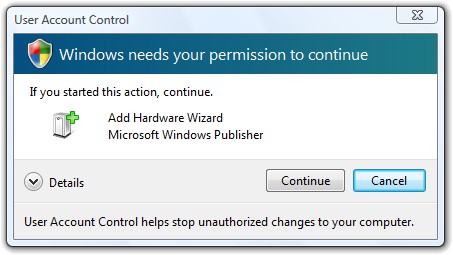
Or in the case of Windows if you have the permissions and security levels on default should see the User Account Control anytime you try to do a change to Windows.

And why should we respect this?
Because of the guiding principle – principle of least privilege, programs, users and systems should be given just enough privileges to perform their tasks.
So taking back the topic about violations and security.
The most common types of violations include:
- Breach of Confidentiality – Theft of private or confidential information, such as credit-card numbers, trade secrets, patents, secret formulas, manufacturing procedures, medical information, financial information, etc.
- Breach of Integrity – Unauthorized modification of data, which may have serious indirect consequences. For example a popular game or other program’s source code could be modified to open up security holes on users systems before being released to the public.
- Breach of Availability – Unauthorized destruction of data, often just for the “fun” of causing havoc and for bragging rites. Vandalism of web sites is a common form of this violation.
- Theft of Service – Unauthorized use of resources, such as theft of CPU cycles, installation of daemons running an unauthorized file server, or tapping into the target’s telephone or networking services.
- Denial of Service, DOS – Preventing legitimate users from using the system, often by overloading and overwhelming the system with an excess of requests for service.
One common attack is masquerading, in which the attacker pretends to be a trusted third party. A variation of this is man-in-the-middle, in which the attacker masquerades as both ends of the conversation to two targets.
This is a common “attack” used to learn the Switchport Security command in Networking courses. You define the max number of MAC Addresses in a port and if the max amount if passed you can shutdown the port or restrict the traffic or connections.
The OS must protect itself from security breaches, such as runaway processes (DoS), memory-access violation, stack overflow violations, the launching of programs with excessive privileges and many others.
We will still be talking about OS and security but it’s all for today folks!!


