--Originally published at Mental Droppings of a Tired Student
Computer security is critical in almost any industry which uses computers. Currently, most electronic devices such as computers, laptops and cellphones come with built-in firewall security software, but despite this, computers are not 100 percent accurate and dependable to protect our data.
There are many different ways of hacking into computers. It can be done through a network system, clicking into unknown links, connecting to unfamiliar Wi-Fi, downloading software and files from unsafe sites, power consumption, electromagnetic radiation waves, and many more. However, computers can be protected through well-built software and hardware. By having strong internal interactions of properties, software complexity can prevent software crash and security failure.
That being said, the answer to the question; why should we study computing security? It depends who is asking. If you’re an engineer, particularly related to computer science, I’d say because it’s your job to know about these things. If you’re a regular Joe who just happens to interact with computers on a daily basis, I’d say it’s better to be safe than sorry.
No matter what age you are, if you’re going to partake in any sort of online activity you should know at least some basic points in how to protect your computer and yourself. Skepticism is your best ally. If it sounds too good to be true it probably is.
Let’s cover some basic security points shall we?
1.Install AD Block
Ad block is a handy plugin to avoid those annoying weight loss or click bait adds. If you’re setting up an elderly person’s computer, or someone who isn’t quite tech savvy, just install it without explaining. They’ll never get it anyway. It also disables YouTube ads so you can watch videos without having Selena Gomez trying to convince you that her digitally enhanced hair is the product of









2. Logging in and out of your accounts.
It’s simple yet people forget to do it all the time. If you’re logging into a personal account in a computer or device that isn’t your own, LOG OUT when you’re done using it. This will save you the humiliation of having someone post an embarrassing status update on Facebook or worse. If you are lending someone your computer, keep an eye on them or let them use a guest session if you suspect they’ll snoop around your stuff.
If you are leaving your computer unattended for a while, even if you’re just going to the bathroom, make a habit out of locking your screen. Believe me you don’t want people sending emails on your behalf telling everyone you’re buying doughnuts for the entire building next week.

3. Passwords and common sense.
Let’s say you bought a lipstick online, and you made an account at the shop you bought it, you paid directly with your credit card. You used the same password you use for your email, and other personal accounts. Let’s say the store you bought the lipstick at was attacked and their customer’s information was compromised. You see unfamiliar charges on your credit card statements. First thing to do: change all the passwords on the accounts that share the same password. Call your bank and report the fraudulent charges.
What is the lesson to be learnt from this example? Never use the same password for all of your accounts, especially if you have sensitive information like credit card information linked to them. Always use different passwords, and never use obvious passwords like 123456… Combining numbers with upper case and lower case letters is the best option.
This example is taken from a true story, a controversy that happened to an indie makeup brand called Limecrime.

4.Online shopping
I only shop online if they accept paypal or if I really trust the company, for example sephora or amazon. Paypal has the advantage of offering buyer protection, though I had one experience where they said the buyer protection didn’t apply to the item I was buying and refused to help me… apparently they decide what applies and what doesn’t so be careful with that. Also check the dates on your buyer protection, if the period has expired you won’t be able to get a refund.

5.Clearing your browsing history
Again, you would think this is an obvious privacy measure, but some people genuinely don’t think about this. All browsers have a record of what sites you’ve visited. If you’ve been in some naughty sites or googled something embarrassing, be sure to delete the browsing history if someone other than yourself has access to this device. Also read point 7 before doing this.

6.Using incognito mode
Google chrome has a nifty functionality that lets you navigate without saving a browsing history. You’ll still be identifiable to the network you are using, and the websites you are visiting, you’re merely navigating without the browser recording a history of the sites you’ve visited. Also AD Block doesn’t run in incognito mode.

7.Mind the network
Always be aware of the network you are using to look at your information. If you want to upload selfies or send pictures, do it when you are connected to your own network at home. For example, don’t upload pictures at school or work using their network since those photos will remain in the router’s cache memory and might be seen by those who administrate the network. They also monitor traffic and can trace who is viewing what within campus. So be mindful of your online activity in networks which aren’t your own, you never know who is watching.

8.Privacy settings in social media
Another no-brainer that gets the best of people is appropriate use of privacy settings in social media accounts. For instance, Facebook has options on who can view what content you publish on your timeline. You can even use your timeline as a personal inbox by setting the privacy setting so that only you can view what is published in it. I personally think Facebook is the main social media account that needs extra attention when it comes to privacy, since it has lots of interactive options such as information, location, personal information, photos. Friends, family, colleagues and teachers all seem to use this platform which is why I am particularly mindful of what I publish there.
Instagram for example is more carefree because it’s just photos, I view instagram as a visual display of a small part of my life and don’t particularly care who finds it. If someone from work or school happens to stumble upon it I wouldn’t particularly mind, if I do mind someone lurking I simply block them. An instagram account can be made private as well, but it defeats the purpose of having an account in the first place. It’s meant to share snaps of your everyday life with everyone, if it’s private your audience is significantly reduced. Same with snapchat, it’s a carefree environment; if you don’t want someone lurking, simply block them and move on.
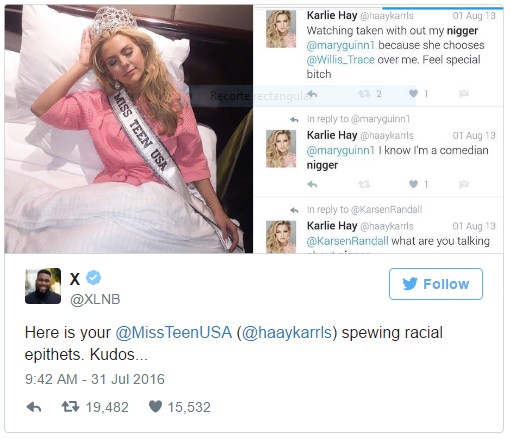
Twitter is often a place where people get in trouble, particularly when expressing their opinions on controversial matters or expressing their views on some topics. As a rule of thumb, ask yourself: Will this get me in trouble if someone were to bring it up later? What if someone were to screenshot it? If the answer is yes I would get in trouble, keep it to yourself. You have to be sure you will be able to justify what you’ve written to anyone who encounters your tweet. Same goes for having conversations via text, if you’re going to say some wild stuff, don’t put it in text, remember screenshots exist.

Full story on Miss Teen USA’s not so smart choice of words here.
Pro tip: If you’re in the process of finding a job, you’ve gone to interviews and you don’t want HR snooping, temporarily de-activate your social media accounts until you get hired.
9.Common hoaxes / Don’t be paranoid
I often see people, particularly older people, share posts on Facebook, usually with an alarmist tone about how the Facebook disclosure policy has changed and somehow posting on your timeline about how you do not consent your photos to be used exempts you of having Facebook do whatever the hell it wants with your information.

Newsflash, if something is free, YOU are the product. But don’t worry, unless you’re a celebrity or a public figure your information isn’t as valuable and can go unnoticed. But seriously stop sharing those types of posts in Facebook it’s embarrassing. Also liking a photo won’t get someone free medical help.

These are just some basic tips I’ve learned throughout the years.
To be continued…

