--Originally published at Mental Droppings of a Tired Student
First of all, I would dare say 99% of people’s passwords suck. Even Mark Zuckerberg’s password was terrible and he is supposed to know a thing or two about computers. Zuckerberg’s Twitter and Pinterest accounts were hacked, with a group called OurMine Team claiming responsibility. They hacked into the Linkedin Database and found Zuckerberg with the password ‘dadada’. Hmm really? Not even a number, a lowercase/uppercase combo? Yes, the 32-year-old Facebook founder, worth $51.2 billion, had a couple of social media accounts compromised by reusing “dadada”.
But I shouldn’t be too hasty to judge, I have a couple of accounts with crap passwords too. Usually these are accounts I don’t care about, they all have the same password, something I can remember quickly. However, upon researching further about passwords I found out my “good” passwords aren’t as fly as I thought they were.
My method is, I have a password exclusive to my bank information. Then I have a different one for paypal. Then I have similar ones for my social media accounts I often use. And finally, I have the same crap password for accounts I will only use once, or I don’t care if it gets hacked. But to be honest my important ones aren’t as strong as they should be, so I’m currently working on making them better.
The use of passwords as a method of authentication is annoying to say the least, because if you have a password that is easy to remember it’s probably a bad one. Furthermore, generally people assume that because it’s a difficult password to remember for a human, it therefore is a secure password; but it turns out these end up being combinations that are easy for a computer to guess with a relatively simple algorithm. So how can we poor humans win


So first thing is first, obviously, any variation of the word “password” is a no. You should be ashamed of yourself if you have that kind of password. I mean, I’m not judging… but yeah I’m judging.

It must be longer than 7-8 characters
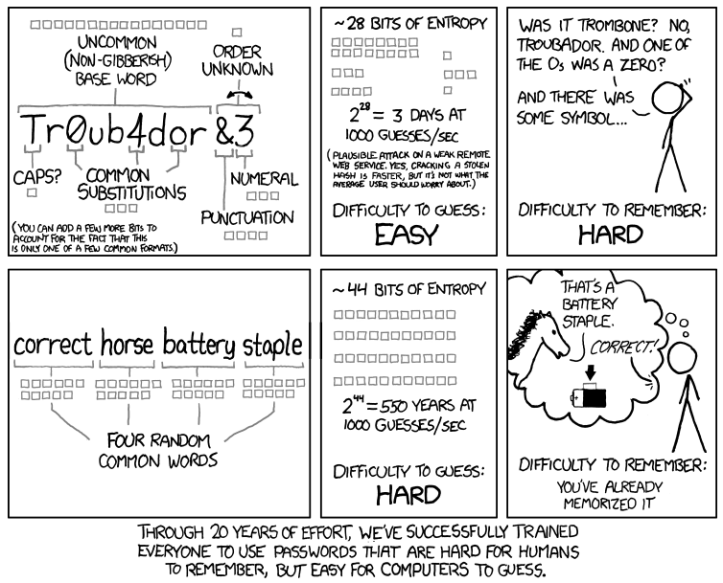
Let’s talk about bits of entropy. It is usual in the computer industry to specify password strength in terms of information entropy, measured in bits, a concept from information theory. Instead of the number of guesses needed to find the password with certainty, the base-2 logarithm of that number is given, which is the number of “entropy bits” in a password. A password with, say, 42 bits of strength calculated in this way would be as strong as a string of 42 bits chosen randomly, say by a fair coin toss. Put another way, a password with 42 bits of strength would require 242 attempts to exhaust all possibilities during a brute force search. Thus, adding one bit of entropy to a password doubles the number of guesses required, which makes an attacker’s task twice as difficult. On average, an attacker will have to try half of the possible passwords before finding the correct one.
So the more bits of entropy you add the more secure your password is. The problem is a seemingly “difficult” password (which is also difficult to remember for the user), can have few entropy bits and therefore easy to crack. As demonstrated by the comic below:

Don’t do common things
I’m talking, replacing and ‘e’ for a ‘3’, ‘1’ instead of ‘i’. I bet you thought you were real slick replacing that ‘o’ for a zero, but it turns out everyone does that. I used to do this myself, so I had to hang my head in shame for a moment. You’re welcome to do the same.
Four random words method
This method is suggested by xkcd.com’s comic above. Four words stuck together is safe against brute force attacks because it’s too long, and it’s conformed by words that can be easily remembered and typed.
So this method has potential, but if you pick fairly common words you end up being vulnerable to dictionary attacks.
Best Practices
- Three to four words together, it can be two common and the others can be uncommon words such as a brand name or something in another language, maybe a band name, etc.
- The use of underscores between words is quite common, but if you place an underscore in the middle of a word, that will make your password quite strong.
- Don’t pick words that can be deduced by your publications or blog entries. So for example, don’t use the name of your favorite band if everyone and their mother knows that’s your favorite band. Make it as random as you can manage, yet easy to remember.
- Don’t re-use passwords. If a site is compromised and your password is released, your other accounts with the same password will also be compromised. Generate a random password if you’re using a site you’re unlikely to use again.
- Using a good password manager is probably the smartest thing you can do. Make a master password and have the password manager do the rest. Of course you have to decide how trustworthy that password manager is. I’m looking into finding a good password manager myself.
Of course this method seems like a life saver but more often than not, websites limit the size of your password to something like 12-16 characters which kills the strategy above and makes your password more vulnerable. Also, there are sites that force you to use uppercase, lowercase letters, numbers and a symbol. Making your password unnecessarily complicated and by no means more secure than it would without these ridiculous requirements. This is why I believe having a password manager is the way to go, at least for these kinds of sites.
For the second part of this post i will be trying my hand on cracking passwords using Jack the ripper. Stay tuned!
References:
http://www.vanityfair.com/news/2016/06/mark-zuckerberg-terrible-password-revealed-in-hack
https://www.explainxkcd.com/wiki/index.php/936:_Password_Strength


