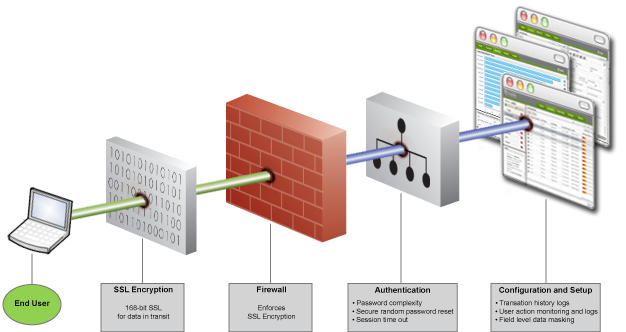
--Originally published at Security blog
For the last post in this semester, we will talk about implementing the system securtiy in our project. Recall that system security talked about things of operating systems and, in my understanding, the more local parts of a software system. Some parts were also given to us, like rules to follow, and they are not so many as they are for the web security, but are also important parts to have in sight.
The password theory we saw, the one that used three things (what we know, what we have and what we are) was a little bit considered, but at the end, once again, we didn’t have time to implement more advanced things. We simply use written passwords. For the other part we saw about this was NTFS, the other file system. We really didn’t see this thing in a bigger sense. We didn’t even use files or anything. The part about that that we could use is the part of the active directory, because of the little amount of objects we use.
One of the things we saw about this is the part of the data backups. This is an important topic, because, obviously, if something happens that can end in a losing of information or cunfigurations, for example, we can recover everything from a previous state. The only thing we must have a backup of is of the database. Our apps will work with a strong basis in the database. The app can know the levels that are unlocked, the results and, of course, all of the users and passwords to grant or deny access. Fortunately, the MySQL service we are using has the ability to create and read text files to reconstruct the database from the point it is. We just have to follow some backup