--Originally published at Computer and Information Security
I used https://github.com/richardgirges/express-fileupload/tree/master/example#multi-file-upload
--Originally published at Stories by Luis Arturo Mendoza on Medium
I used https://github.com/richardgirges/express-fileupload/tree/master/example#multi-file-upload instead Multer, with that I didn’t need to save the file in local storage and make easy to send it to S3.
Hope to help you!
the end of devOps
--Originally published at How to HACK or not
The last month I used some of my time to learn and remember some stuff about devOps, linux, git repositories, setting up servers and the use of tools like cron. As I said some of this activities were more to remember knowledge that I mostly had in my networks classes or operative systems; but in the majority this activities were new to me, some of them I never tried them before and I have to say it was fun.
Part 1, part 2, and part 3 of my adventure learning some of devOps can be found on those links in another of my blog entries. You’re free to read them, those are short and maybe funny. I will summarize for you what you will found if decide to read the posts:
In part 1 I wrote about how wrong we are people with the concept of devOps, like it’s completely different of what we think, well not that completely but yeah no ones knows exactly what it means or what to do when working on DevOps.
In part 2 I installed a linux distribution with a virtual machine in my laptop along with python and java and some other tools to start working with DevOps, basically was setting up the environment to be able to do something.
In part 3 we started working! This was a difficult task, I had to create cron jobs, and start automating stuff of my repo using my my tiny and slow window of linux, it was fun though, but I don’t think this is something I would do for living haha.
In general I loved/hated this activities because:
- Is something a haven’t done in a while, so doing something different from what I am used to is good, it’s like relax BUT Continue reading "the end of devOps"
Python Unit testing
--Originally published at How to HACK or not
For this blog entry, we are focusing in unit testing on python. While doing some research it’s kinda similar to JUnit (for unit testing on java) and it’s python (my first programming language) so I hope it be as easy as it sounds.
First I read an article recommended by our professor about small talk and testing on it using a framework to support it. Interesting article, but most useful is the tool Hypthes.is which allow us classmates to make annotations on the document so we could share our thought about the paper.
Also, we could read the paper thanks to Wayback Machine which allows to see all versions of some websites so, while I was on this I use the occasion to look into a website I like to see how it looked years ago. I chose instagram because is my favorite social network and app, I obviously knew that there wasn’t a website since the beginnings but I had the doubt of what they used to show and I found this:
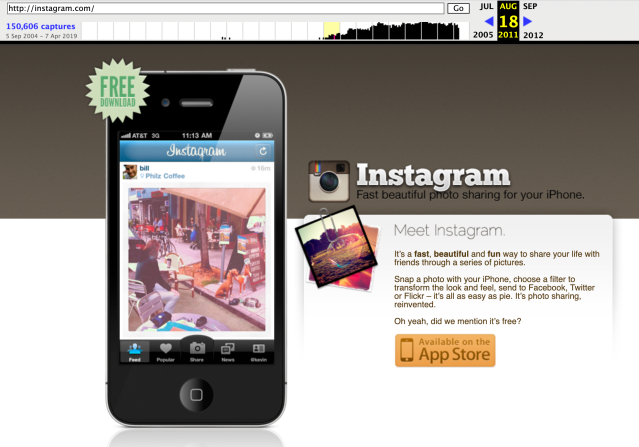
It’s nostalgic to see the old version of instagram before Facebook happened. I think Instagram have one of the best app designs (until their last update that I don’t love) but the oldie one is pretty pretty, it would be nice to have a feature like use the old design or something. But well… let’s continue with python.
For this task we had to look into a LinkedIn course about using PyCharm for unit testing on python: Unit Testing and Test Driven Development in Python course. First we defined some test cases
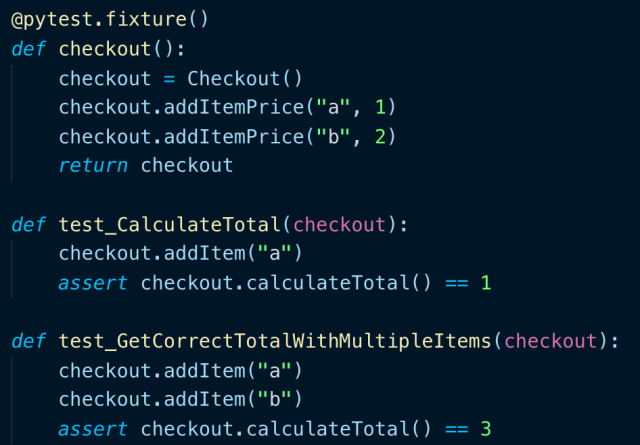
and then we run them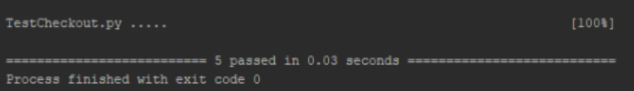
At the end all test cases were successful and the tutorial was fun to do. I truly feel I have learned something new and useful because the course Continue reading "Python Unit testing"
Review week 11
--Originally published at How to HACK or not
We were able to finish the map screen and also the start screen, where you introduce the bici’s code, for the presentation and also we made a power point for it.
Bellow there are attached some images of the obtained results :
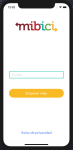
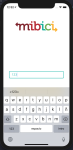
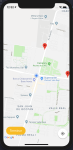
Plan week 11
--Originally published at How to HACK or not
This week we will continue working with the implementation of the app in relation to the api of google maps, we will perform GPS location tests and so on.
We hope at least finish this part, the map view and the current location sending in intervals of n meters away to be able to present it in the next week presentation, that also we will have to prepare it.
Review Week 10
--Originally published at How to HACK or not
For this week we did work with the Google Maps API by adding it to our application. The main concern was to add some functionality to the app using the maps, but while working on it we realized we still need to figure it out what exactly will the user see in the app, just their location or what. We already can do that in our app, so we kinda accomplish what we proposed but its not finished yet.
Plan Week 10
--Originally published at How to HACK or not
For this week the main task is to follow the work with the Google maps API integration. We already inserted it into our app, but we still haven’t connected it yet to the functionality of the app. So for this week two main points:
- Correctness of the google api integration.
- Add functionality, we need to do something with the maps and not just showing them (that’s useless).
Intro to DevOps part3
--Originally published at How to HACK or not
Now, in this entry we’ll see Intro to devOps volume 3 (I love Guardians of the Galaxy movies). This is the third part of the blogs about devOps and how to setup a full environment for deployment, automation, etc. using a linux machine. In this part I’ll talk and try to do the setup for GitHub, ssh and keys.
The first step in this part is to have a GitHub account which I already have (yay), you can review it here. Now I should create a repo for testing this, the teacher said we should use some web content, it is the most common thing nowadays I suppose. So, for this I will use a repo that I used to learn and practice Angular.
I lost some time because by looking at my profile, something I don’t use, my first years in GitHub were basically nothing in terms of contributions compared to now and it’s because of my different jobs, it’s great companies use such useful tools like GitHub.
Okay, now I realized that I should’ve went by the Node way when installing web servers because it’s what I usually do haha, so let’s do that “how to install node in ubuntu and after that we can continue.
Next is setting up my two factor authentication on my GitHub account which I have already did before. And for the SSH keys, I have created them before but I need to create one for my linux machine. Usually this is easy, but oh yisus it’s difficult to do it from a virtual machine! and I don’t use the same commands as for my Mac so ugh…
After that I cloned my GitHub repository and made some changes to see it actually works, made some modifications and yeah, everything perfect.
Intro to DevOps part2
--Originally published at How to HACK or not
This is the second part of my blog Intro to DevOps, which I wrote two weeks ago. In this part I’m installing a Linux distribution, installing support for development and at last setting up the first test of Cron.
I’m using a MacBook Pro 2016 and I don’t want to deal with all the complicated stuff to install linux right on hardware so I am using a virtual machine from Oracle, VirtualBox. Last time I installed a Virtual Machine and a Linux distribution was in my Networks class two years ago, so let see if I don’t get in trouble.
First, this is newer version of virtual box that the one I used previously so I’m dealing with “where do I click to install the linux distribution”. Oh, I downloaded Ubuntu Desktop, btw.
I thought I was installing the version with no UI, but it does, so it’s new for me too. It’s taking so long… Ok! it’s done, I have Linux Ubuntu in my Mac. Now, the next step is to setup my programming languages, I think I’m just gonna install Java and Python.
Installing java was so hard, I don’t know if I went for an incorrect path or what, I don’t even know if I actually installed it. Python 3 was much easier, just a few commands and that was it. Now GitHub, it should be easy… and it was :D. Next I have to setup web deployment, for this I’ll go for LAMP, it’s something I have done before. For this I’m following the instructions on How to install LAMP Stack on Ubuntu and it was just fine, long, but not hard.
Now, the last thing to do in this blog is to setup the first test use of Cron on the server. Okay, I Continue reading "Intro to DevOps part2"
