--Originally published at PocketMinder's Blog
So, how important it is to create a good security architecture?
If your answer is something similar to “not that important” then you are screwed my friend.
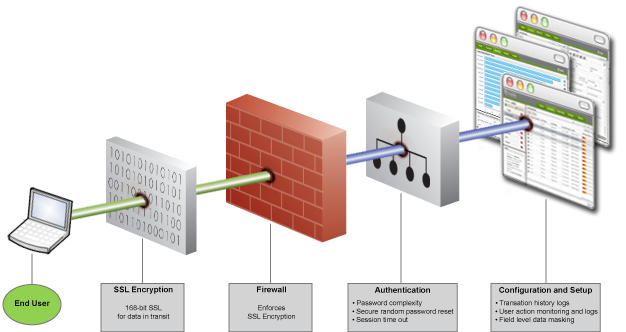
It is VERY important to create and maintain a good security architecture, because if you don’t do it properly, following the steps necessary to ensure minimal risk, then your system will fail, and depending on the type of information your system handles, it can be very bad.
A good security architecture is one where it is being planned and developed in parallel to the actual system itself, having a good foundation so that any other new features the system will implement can actually be implemented properly. It cannot be bolted on to the system, if it is, then how can you be sure that there are no flaws?
Another important aspect to the security architecture of the system is the testing, if you can’t test the security properly, then it is not well-implemented. You must check every single aspect of the architecture to make sure you have a good security architecture, otherwise it is like shooting in the dark!
Again, security is pretty much the most important aspect of any system, and depending of the type of information handled, then it can be critical to the success of the system to have a really good security architecture, and also well documented, because no one wants to bang their head trying to figure out what the heck a variable is doing to the overall security of the system.