--Originally published at TC2027 – Computer and Information Security
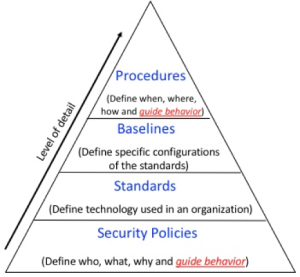
In my latest post I talk about what are security policies and what a security policy contains but how do we apply a security policy? With a security model.

A security model is used to determine how a security policy will be implemented, what users can access to the system and roles. This security model describes the entities governed by the policy, it states the rules that constitute the policy.
There are many types of security models according their scope, for example
- Capture policies for confidentiality such as Bell-LaPadula
- Capture policies for Integrity such as Biba, Clark-Wilson
- Models applied to environments with static policies such as Bell-LaPadula
- Models applied to dynamic changes of access rights such as Chinese Wall
And many others but I’ll talk about some of them.
How can we differed model from policy, easy a model is maps the goal of a policy by using data structures and techniques that are necessary to enforce the security policy.

State Machine Models
In this model the state of the machine is captured in order to verify the security of a system. Each state provides permissions to objects and access subjects, if the subject can access to the object only by mean that are concurrent then the system is secure.
For the im0lementation the developer must define what and where the states variable is, the developer then must define a secure state for each state.
Bell—LaPadu Confidentiality Model
This model was the first one to define with a multilevel security policy for the states. This is a static model which enforces the confidentiality of the model. This model focuses on ensuring that the subjects with different clearances (top secret, secret, confidential) are properly authenticated
Rules