--Originally published at El Machetero Blog´s
Now that the term has gotten popular let´s talk about DoS attacks. A few weeks ago we heard that sites like Twitter, Spotify and Reddit went down a few hours because of a “cyber attack” known as DDoS. Gizmodo did like a thousand posts about it and if you want to hear the whole story and how this was not the conventional DoS you can do it here.
http://gizmodo.com/this-is-probably-why-half-the-internet-shut-down-today-1788062835
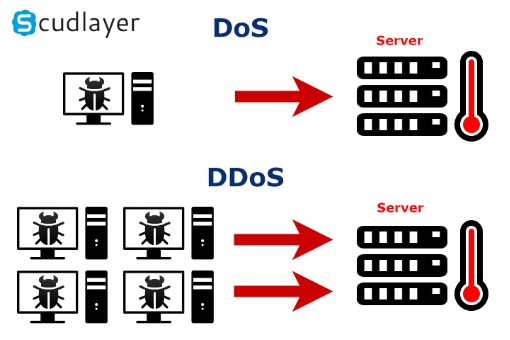
DoS stands for Denial of Service, it is essentially bringing down a site by over flooding it with traffic, so much that it cannot handle it . This can be achieved either by doing the so called ping of the death, that is taking advantage of the TCP/IP protocol that allows an ip packet to be fragmented, the trick is to send pings with a header of bigger size causing the system to crash also DoS can be done by doing a Teardrop attack, it also takes advantage of TCP/IP fragmentation sending confusing headers in the packets so that it cannot be reassembled, causing sooner or later the system to crash.
There are four common categories of attacks:
- TCP Connection Attacks: This type of attack attempt to occupy all the available connections and even devices capable of maintaining millions of connections can be taken with this.
- Volumetric Attacks: Here what they do is attempt to consume the bandwidth either of the target network or between them and the rest of the internet.
- Fragmentation Attacks: Basically they send a ton of TCP or UDP fragments overwhelming the ability of the target to reassemble them and reducing performance.
- Application Attacks: This attack attempt to overwhelm an specific aspect of an application or service, making it able to succeed even with a few attacking machines and because of this they generate a low rate

 traffic, so it’s hard to detect.
traffic, so it’s hard to detect.

And to increase the effectivity of some attacks there are two ways to increase the traffic they can send:
- DNS Reflection: By forging a victim’s IP address, an attacker can send small requests to a DNS server and ask it to send the victim a large reply. Every request can be amplified as much as 70x in size
- Chargen Reflection: Some computers and printers allow an outdated testing service called Chargen, which allows someone to ask a device to reply with a stream of random characters.
We also want to clarify that DoS and DDoS are two different things. DDoS attacks stand for Distributed Denial of Service the difference is that a distributed attack comes from multiple machines performing the attack while simple DoS comes from a single source.

There are hundreds of DDoS attacks every day to some of the biggest companies in the world. Many of this DDoS attacks fail because the companies are well aware that they are targets of receiving this type of threads so they invest many resources securing their company. But sometimes, it doesn’t matter how secure the company is, the DDoS attack can succeed. There’s have been some famous DDoS attacks this past century, and here are some of those:
The first attack we are going to talk about is the one where anonymous attacked the Scientology Church. Anonymous, which is a very popular hacktivist group, made their attack in January 8, 2008 and they named it Project Chanology. The reason this group of hacktivist did this was because they were against the Scientology Church practices and philosophies. There was an interview of the actor Tom Cruise that was taken down by the Church, and Anonymous felt like they were covering up something. So they organize this DDoS attack and they shut down the Church’s website for a moment.
The second attack is about a group called Occupy Central attacking the Chinese government. This so called group Occupy central was formed because of their insatisfaction of the Chinese government. Occupy Central didn’t like the government wanted to apply a one man one vote system for electing people for a political charge. So in June 2014, this group make a DDoS attack to one of China’s major political website.
And the third and last attack we are going to talk about is the one to the BBC’s global website. This attack is consider of the biggest DDoS attack ever. This attack was made by a group called the New World Hacking. What they did basically was shutting down some of the BBC’s sites and also Donald Trump’s website. They use a software called BangStresser, which can launch an attack up to 602 Gbps to any website.
References
- http://www.cyberdefensehub.com/famous-ddos-attacks/
- http://searchsecurity.techtarget.com/definition/ping-of-death
- http://www.digitalattackmap.com/understanding-ddos/
In collaboration with
Alejandro Carrillo and Kimberly Luna


