--Originally published at El Machetero Blog´s
Como ya he mencionado anteriormente, trabajar con personas puede ser algo realmente complicado y aún más si no existen reglas, es por esto que las compañías crean sus propias reglas, específicamente para la parte de seguridad las nombran políticas de seguridad, que son documentos en los cuales se especifican los requerimientos que se deben de seguir con el fin de minimizar riesgos. Existen varias políticas de seguridad, dependiendo del área y la razón por la cual se creará.

Las políticas de seguridad deben definir:
- A quien aplica
- Quien aplica las acciones definidas
- Cuando se deben de aplicar las acciones mencionadas
- Donde o en que equipos aplica
- A que parte de la organización aplica
- Quien hace que se cumpla
- Cuales son las consecuencias en caso de no cumplir con lo establecido
Uno de los objetivos que se buscan al hacer políticas de seguridad es preservar los principios del triangulo CIA. Así que hazle un favor a tu jefe y a ti mismo y sigue las reglas.









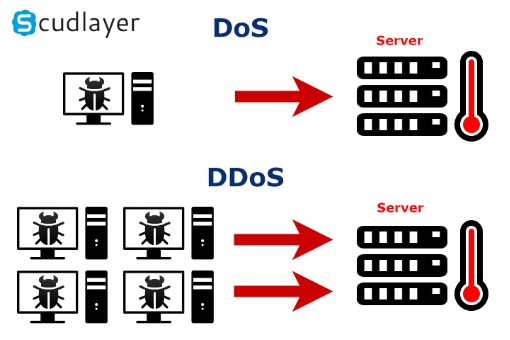








 . But you may ask, how the hell does bad people managed to get into the company D:, well you may have some pretty bad physical security, or bad guys are pretty good at what they do.
. But you may ask, how the hell does bad people managed to get into the company D:, well you may have some pretty bad physical security, or bad guys are pretty good at what they do.

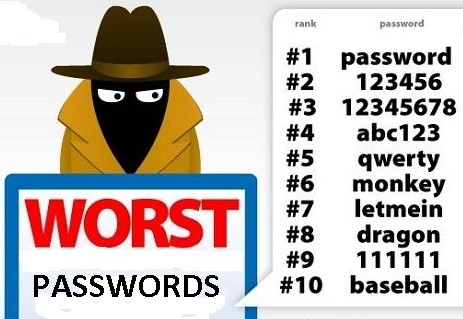












 , even when it´s not.
, even when it´s not.

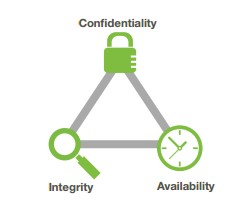

 This means that only authorized persons can access the information, because you wouldn`t like someone else reading your personal information or something that is for a specific person or group.
This means that only authorized persons can access the information, because you wouldn`t like someone else reading your personal information or something that is for a specific person or group.









