--Originally published at The shield of the world
So today post is about Authentication and Access Control…which is something not so new for someone who actually respects the base configuration of Windows (Yeah…right) permissions about new software and modifications and also for the Unix base OS with sudo.
So in the more basics words Authentication is when we identify ourselves to the OS, with an username and a password. So authentication is in reality so simple, just helps the OS to verify that the individual or “user” we claim to be, is indeed ours.
Actually when you are on the same network as others computers and you want to access the information on them, you got a pop-up asking for an specific user and password. This is to authenticate that you are trying to get your own information and not someone else.
We have seen movies where the authentication is almost a ritual, first the person just stands by and uses his password of 4 digits, then in the other door he puts his fingertip, on the other one he uses his eye to authenticate himself and finally he almost have to sing or dance or pray to the gods looking for it to work and access the most secret place and treasure.

Of course in real life there is a high chance that you don´t even have the user and password authentication enable. We are lazy, yes we are… but we need to know when to block our PC and avoid those email for the entire enterprise saying “DONUTS ON ME”, no, I haven´t suffered this, but someone in my group did.

Is not entirely necessary to implement the full ritual that I just mention to you, but a 2 factor authentication can help us to avoid getting our information filtered. When you lost





If you ask me, is cool that more enterprises related to user information are implementing this, probably the banks are ones of the first in using a 2 factor authentication, with that message saying “Oh sorry, you need the Token to do that”. So… some factors to utilize as another authentication source is the username and password, the smartphone app and your fingerprint or retina or a voice message ooooor SMS passcodes, Phone callbacks, mobile passcode like One time password app.
So even if you have a username and password, but you use the password “password” is almost useless, so a 2 factor authentication can prevent from someone else sniffing around your accounts and information. Is your fault for using such password, but I’m a nice person and that’s why I’m suggesting you to use a 2 factor authentication.

Let´s now talk about Access Control, we indeed have seen this at least once in Windows and is the everyday tool in Unix systems.
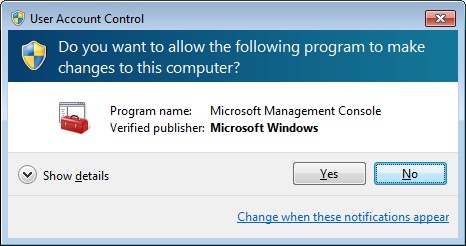
On Windows we see this little windows every time we want to do something like installing a new software, messing around with the registers or something that may damage the OS.

And basically UAC limites application software to standard uses privileges until an administrator(you) authorizes an increase or elevation. By doing this just the applications trusted by the user may receive administrator privileges and this will help us to stay away from Malware. So even if our account has admin privileges the UAC help us prevent unauthorized behavior from random or strange apps. Even if by mistake the admin user open and run the app it will ask for permission before actually letting the app run free.
And this is exactly what happens in Unix with the sudo command. But why not explain the same again… sudo or “superuser do” allows the user with proper permissions to execute a command as another user, such as the superuser…yes when you type su is for superuser… and not this is not a good practice when you are working in Linux-Unix.

But there is a little more security level here… even if you type sudo before the command you want to run, it will ask for the password of the user… is not like thaaaaat secure, but it is something. When you authenticate yourself again, because we have to do this to actually enter to the OS, there is a time stamp where the user can call commands without the need of writing sudo again, this will happen for 5 minutes and after that you need to use sude again.
So this seems pretty insecure, but to actually write sudo and do something we need to be on the sudoers list, if we are not there when we are trying to call sudo, it is considered an unsuccessful attemp to breach system security and mail is sent to the proper authorities(don´t really think so…but who knows) as defined at configure time or in the sudoers file. The default authority is root.

So as we learned today authentication and access control are some of the best ways OS has to protect us and to improve the security of our information and data.
Hope you like it and CY@ Folks!!

All gifs are from Giphy!


