--Originally published at TC2027 – Computer and Information Security
This is the first time that I take classes with ken and I have to say that it is a different experience. I have to say that this is the first time I try blogging and honestly, it’s not my deal. I’m not at good as many other bloggers out there, but the fact that I dig into the topics and subjects by myself it’s a very rich full experience. I think that this way might not be for everyone, because many persons are used to expect for the teacher to receive the knowledge, but if you dig and investigate on your own you might have found a lot on information out there in the internet.
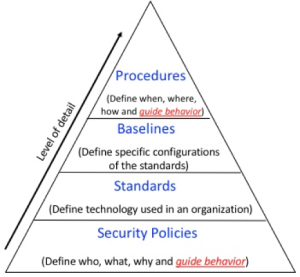
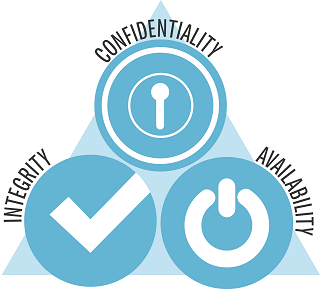
The course TC2027 was focus on system security and I got to say I learn a lot, not only digging in the mastery topics, also in classes one of the things I like most of the course was the applied experiences that ken or the students share, from there I got to learn a lot of new apps or techniques to enforce my personal security in informatics. I learn about vpn’s, about encryptions, about sql injections, about malware, about personal security, about scams and phishing and one of the most valuable things I learn is that there are a lot of blogs of interest that I now follow to get me updated about security or other stuff.
One of the things that I would recommend for the course is to take your time because each topic it might get much more extend than you think and one post might not cover all of it.




 For example key base is an encrypted related app for mobile and computer to maintain information secure. This is a web link
For example key base is an encrypted related app for mobile and computer to maintain information secure. This is a web link